Identity document forgery is a severe offense with potentially severe consequences and regulatory problems for businesses. Criminals misrepresent the government and the law and scam businesses for their gain by inventing or manipulating documents. According to the U.S. News & World Report Identity Theft Survey 2023, the largest number of identity theft incidents reported to the FTC in 2022 were related to credit card fraud, with more than 440,000 incidents. A forged Maltese passport can be purchased for $4,000 on the dark web, a forged Bulgarian passport for less than $20, and a forged New York driver’s license for less than $60. These alarming statistics highlight the importance of robust document verification.
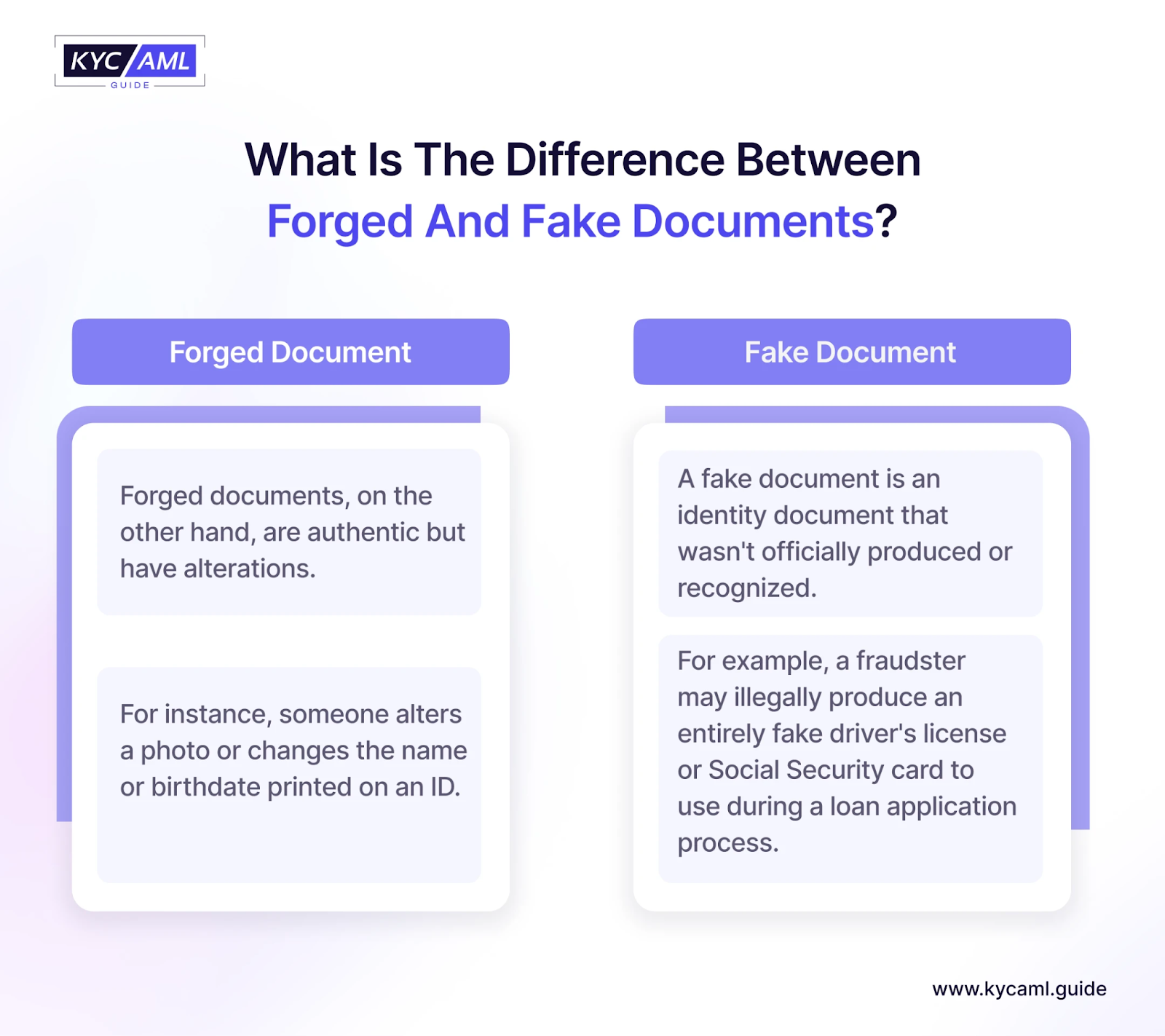
It is important to distinguish between fake and forged documents. Forging and using fake documents may seem similar, but the difference lies in how they are created. While fake documents simply copy original documents, document forgery uses files from legitimate sources and then modifies them. For example, a fake document may bear the signature of another person and be linked to an official document for validation.
How to Identify Forged Documents?
To stop fraud and guarantee the authenticity of important documents, it’s critical to identify fake documents. Using KYB and KYC procedures is the most effective technique to identify identity document forgeries. This process examines customer legitimacy and controls risk based on customer data, transactions, and behavior. Here are some tips to identify forgery.
1 Confirm the Validity of Documents
Document examiners must check official documents for authenticity or discrepancies to identify a forged document. Here are some features of original documents to look out for:
| Paper Quality | Check if the paper does not match what you expect from the original document, such as thickness, texture, or color. |
| Watermarks and Security Features | The easiest way to tell the difference is to look directly at these features. Many official documents have intrinsic properties that are more difficult to reproduce. |
| Alignment and Margins | Simple elements such as misaligned text, irregular margins, or irregular spacing can indicate alteration or forgery. |
| Wear and Tear | The age of a document is a useful way to assess its validity. A warning sign can be a strange new appearance in a document supposed to be outdated, or vice versa. |
Gov.UK provides a guide on examining identity documents.
Also Read: Common Mistakes to Avoid in KYC Document Verification Process
2 Streamline Document Verification with Tools
Using special document verification tools can often speed up the verification process. Here are some tools that can help you scan physical documents manually.
| Magnifier | Use a magnifier to see details that normally cannot be reproduced on a fake, such as the fine print for terms and agreements. |
| UV light | Some documents have smart security features that can only be seen under UV light. A forger who is new to identity document forgery may not be able to handle document forgery well.
|
| Transmitted light | Using light from above, a lamp, or a torch to shine light through paper is a good way to see watermarks and any damage to the paper.
|
| Forensic Analysis | Deeper cases may require forensic analysts who can perform detailed analyses. An expert should be able to look into paper fiber analysis and ink age determination. |
3 Improving Document Verification with Technology
There have been many advances in fraud detection technology. You can benefit by incorporating these features into your company’s document verification processes. With this solution, you can quickly verify the authenticity of your data with a simple method when viewing legal and personal documents. Modern technology can test several things:
| QR codes and Digital Seals | Today, modern documents can have QR codes or digital stamps, which can be scanned into official databases to verify their authenticity. |
| Digital Forensics | For electronic documents, you can use metadata analysis and digital forensic techniques to detect unauthorized changes. Sometimes it is also possible to check the origin of digital documents. |
| Optical Character Recognition (OCR) Software | OCR converts documents into editable data, which is necessary to track changes. |
| Machine Learning and Artificial Intelligence (AI) | AI detects document inconsistencies and improves detection accuracy through learning. |
| Biometric Verification | Biometrics uses biometric characteristics to verify identity, which is important for digital access and security. Selfie Verification uses facial recognition technology to compare a person’s live selfie with an ID photo. |
| Blockchain Technology | Blockchain provides a secure and immutable ledger for document storage, ensuring that changes are tracked. |
4 Utilize Effective Fraud Detection Software
Some fraud detection software uses technologies such as artificial intelligence and machine learning to perform KYC and KYB procedures. This can help you protect your business quickly and in real time. One of the biggest advantages of using fraud detection software is having access to a large database to cross-reference and verify data. This can help ensure that your reviews are accurate and well-informed.
By following the steps mentioned in the picture you can identify fake driving license and passports.


Safeguarding Business: Strategies to Prevent Identity Document Forgery
The bad news is that fake or counterfeit ID cards, passports, or driver’s licenses could one day end up in the customer verification process. The good news is that you can keep your system safe and fraud-free by following these steps:
1 Prioritizing Authenticity
Fraudsters pay more attention to visual similarity with genuine ID documents during identity document forgery. But they often miss important details that cannot be seen with the naked eye. This is where KYC identity verification solutions come into play. For example, forged biometric documents often fail RFID chip verification. The RFID chip is the most difficult security element to counterfeit, so it must be checked first. Advanced forgeries involve the use of cloned chips, but can be detected by server-side chip verification. If you have a reliable document reader, you can detect small changes in visual inspection zones (VIZ), machine-readable zones (MRZ), and lack of safety features such as photos or lenticular images.
2 Complete Identity Verification Solutions
As more and more verification sessions are conducted online, you need to avoid vulnerabilities in your systems that could be exploited by attackers such as low document security, legal loopholes, and low privacy awareness among customers. A well-designed identity verification solution collects user data, such as customer ID scans or selfies, and sends it to the company’s servers, where another component performs authentication checks.
You can find out the best solution for your business needs by following the guide “How to Choose the Best KYC Solution: A Comprehensive Guide?”
3 Leverage Liveness Checks
Biometric identity documents are less likely to be forged as they are equipped with a range of sophisticated security features, which explains their growing popularity. Scammers come up with tricks that work in unsecured remote meetings. Fortunately, many attacks with fake printed images, video replays, injections, and 3D masks are detected by liveness checks. It allows you to verify the authenticity of a photo, whether it’s a portrait or a passport scan.
Also Read: Harnessing Liveness Detection in Selfie-Based Digital KYC
4 Examine IP addresses
In a remote situation, you can track a customer’s IP address while they are sending data to your systems. Additionally, you can create a blacklist of suspicious IP addresses to stop sessions and block future traffic from them. For example, a session where a client with an India IP address claims to live in Brazil should raise a red flag. Additionally, it is worth paying attention to repeated attempts to log into your system from the same location. You should also be aware of situations where you repeatedly receive data from different geographic regions.
5 Utilize Extensive Databases
Governments regularly update identity documents to address the rise in identity document forgery. So to reveal any fraudulent changes, you will need recent sample documents for reference. This means that all trusted identity verification tools must store multiple versions of each identity document and passport in their database. You will then receive a notification when a customer presents an outdated document that has already been withdrawn from circulation. An extensive database of document templates also protects against false positives.
KYC AML Guide: Your Go-To for Finding the Right Identity Verification Solution
In short, it’s pivotal to involve effective techniques for spotting and preventing identity document forgery. By utilizing advanced technologies we can reduce the risk of fraud. KYC AML guide provides KYC technology buying and vendor analysis consultancy. Our goal is to assist you in finding the ideal identity verification solution that aligns perfectly with your business needs.







