Introduction to Biometric Identity Verification System
Earlier in the 1800s, the Biometric Identity Verification System was first introduced in Paris, France. Alphonse Bertillon developed a specific method of classification for criminals through body measurements. Subsequently, the system, even after having loopholes paved the way for biological characteristics for identification. The system of fingerprint identification also dates back to the late 1800s. Sir Edward Henry of Bengal Police was the first one to establish the fingerprint record system in London.
Confusion between Henry Faulds and Edward Henry
Sir Edward Henry is not to be confused with Henry Faulds, who is known as the father of forensic fingerprinting. Henry Faulds was never credited in his lifetime for being the pioneer of fingerprint identification. Following his footsteps, Sir Edward Henry took his mission further and established the first-ever recorded fingerprint classification system in 1896.
Evolution of Biometric Identity Verification System
Over the brief historical period of a century, the Biometric Identity Verification System evolved, and new modalities were introduced. Today, the Biometric IDV System stands as a basic requirement for every financial institution and bank. As of 2016, 57% of companies use biometrics for authentication.
Moreover, the following timeline explains the evolution of the Biometric IDV System in detail.
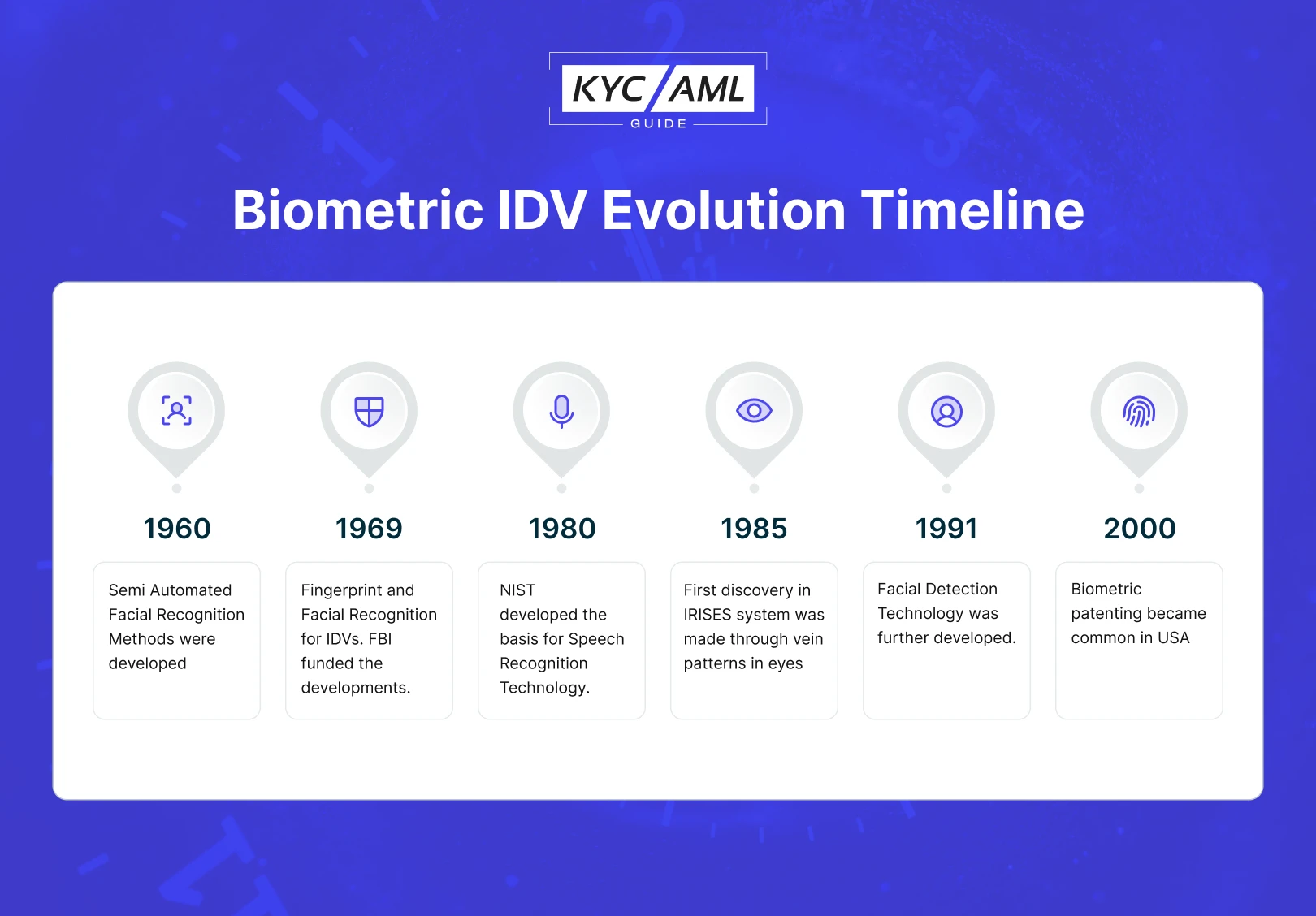
A Decade of Widespread Biometric Identity Verification System
Since the last decade, biometric systems have been widely used. Also, the advancement in biometric technology increased a lot. Rapidly, companies switched their authentication and identity verification to Biometrics for seamless processes. For example, in 2013, Apple introduced the fingerprint lock in the iPhone. As the concept evolved and widespread, most smartphones now have fingerprint identification and authentication functions.
Biometric Implementation Updated Statistics
- According to Statista, the Biometrics system revenue market will rise in the coming years. In 2022, it was recorded at $43 billion. By 2027, it is expected to surge to $83 billion which is nearly double the last year’s statistics.
- A report by GetApp estimated that in 2019, 64% of US companies implemented 2-factor authentication and this percentage increased to 92% in 2022. Similarly, the use of Biometric Authentication tripled from 27% in 2019 to 79% in 2022.
Types of Biometric Identity Verification System
Currently, the main types of Biometric IDV Systems which are widely used are as follows:
1 Fingerprint Recognition
As discussed above, fingerprints have been used for quite a long time for identity verification. It is a biometric IDV in which fingerprint patterns, friction ridges, and other techniques are used to identify people. Notably, numerous methods are used for Fingerprint IDV, such as optical fingerprint recognition, capacitive sensors, and ultrasound fingerprint.
2 Voice Recognition
Voice or Speaker recognition has two further types:
- Text Dependent – It is triggered with a phrase or password that was spoken before actual VR starts
- Text Independent – It recognizes an unpatterned or unconstrained voice as long as basic data is provided
Usually, it is a combination of both aural and physical components of voice. Pitch, Depth, Tone, and accent matter in VR. Given that, VR is widely used when a person is unable to provide fingerprints. Likewise, it also helps the blind person in many situations.
Also Read: Biometric Voice Recognition
3 Iris Recognition
Usually, Iris recognition and Retina Eye Scan (RES) are confused to be the same identification processes. Actually, they are different as Iris involves the identification of an individual by analyzing the unique patterns in the colored part of the eye. Iris Melanin is transparent in infrared light. So, the unique pattern in melanin of every eye can be differentiated easily. It enables a high level of identification in a large population. Previously, Iris recognition was outwitted by the pictures of eyes, but the latest Iris recognition is much more advanced and fool-proof. Now, Iris IDV Systems can also detect the liveliness, temperature, and moisture in the eye to make it more accurate.
4 Vein Pattern Recognition
Likewise, the blood vessel pattern is proven to be different in every human being. Which is why infrared light can be shed on a specific body part. Based on the principle of photographic reflection, the image of this pattern can be identified. Vein Pattern is the next level of the Biometric Identity Verification System. However, it is still uncommon in many regions of the world.
5 Face Recognition
Facial Recognition is by far the most demanding Biometric IDV System. Mostly, the concern is that a person is not wearing a mask. Automatically, Face Recognition detects the features of an individual’s face in 3D or 2D dimensions. The system can be outwitted through photographs, masks, make-up, and most importantly deepfakes. Besides, scientists are working on developing facial recognition systems that are much more complex. Through embedding Artificial Intelligence and other technologies, this IDV system is the future. Currently, smartphones also offer facial recognition phone locks.
Also Read: NFC Identity Verification
Use cases of Biometric IDV System.
- Mumbai Terror Attacks – 2008: Biometric technology was used to identify the attackers and track down their accomplices.
- Boston Marathon Bombing: Suspected were identified using Biometrics.
- London Subway Bombing 2005: Biometrics facilitated the identification of suspects.
- Paris Attacks – 2015: Biometric technology helped in identifying terrorists involved in the attacks.
- Orlando Nightclub Shooting: Biometric technology was used to confirm the identity of the shooter.
Banks using Biometric Identity Verification System
| HSBC | Through voice recognition technology, it quickly and securely verifies customer identity, reducing the risk of money laundering. |
| Barclays Bank | Uses a Biometric IDV system for their mobile banking app. It allows customers to securely access their accounts using facial recognition or fingerprint scanning. |
| Bank of America | It has integrated biometric identity verification into its mobile banking app, using a combination of facial recognition and voice biometrics to securely authenticate users. |
| Standard Chartered Bank | It uses biometric identity verification through face recognition technology to quickly and easily verify customer identity. Also, to reduce the risk of fraud and money laundering, it has been useful. |
| JPMorgan Chase | It has integrated a biometric identity verification system in its mobile banking app verification. Thus, using facial recognition technology to securely and conveniently authenticate customers. |
Challenges in Implementing Biometric IDV Systems
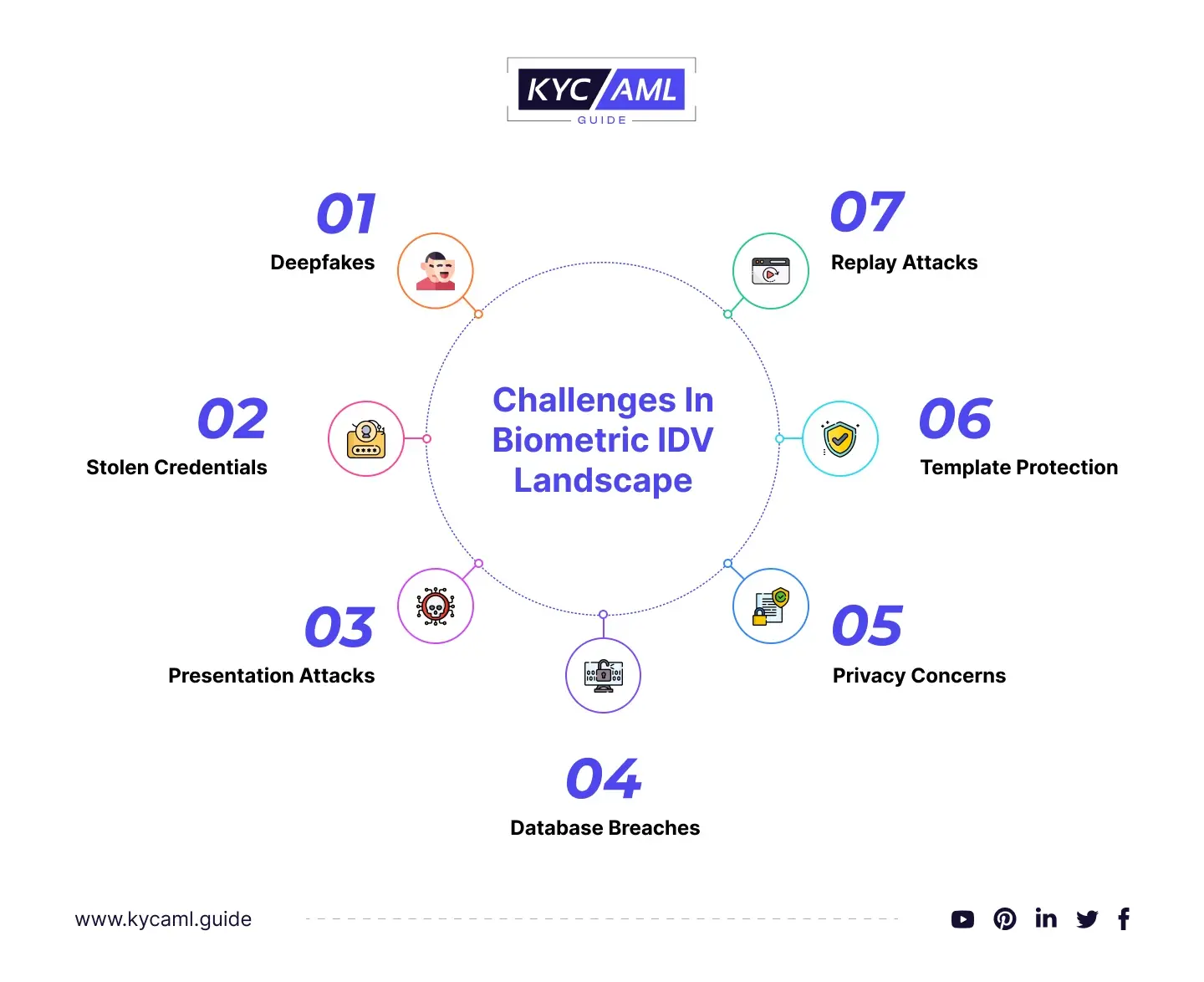
| 1 | Deepfakes | Highly realistic facial images and videos, potentially fooling facial & voice recognition systems. Deepfake is a way of outwitting these systems and is a crime in most jurisdictions. |
| 2 | Cross-Modality Attacks | Attackers exploit gaps between different biometric modalities, such as trying to use a 3D mask to impersonate a real face. It is different from a deep fake as deep fake uses digital technology for impersonation rather than a mask. |
| 3 | Device Variability | Variations in biometric data acquisition devices can affect the accuracy of recognition systems, requiring strategies to handle such inconsistencies. |
| 4 | Biometric Data Storage | Poorly managed Biometric data storage can lead to hacking, unauthorized access, and regulatory non-compliance. |
| 5 | Aging and Variability | Biometric traits can change over time due to factors like aging, injuries, or health conditions, posing challenges to maintaining accurate recognition over the long term. |
| 6 | Replay Attack | Attackers may record and replay biometric data to gain unauthorized access. Multiple attempts can cause the system to crash or malfunction or simply authorize attacker access. |
| 7 | Imposter Attacks | Fraudulent Attempts where an attacker tries to impersonate a genuine user through various means. Identity theft is one of the most common methods to do so. |
| 8 | Liveness Detection | Developing effective methods to detect whether the presented biometric data is from a live person or a recording. Poor or no liveness detection can let the attacker penetrate the system easily through any of the above methods. |
Robust KYC through Biometric Identity Verification System
Overall, the above discussion talks about Biometric technology and how it is useful in identifying someone. KYC (Know Your Customer) is a practice in which the data for customer identification is collected and verified so the link between the two concepts is quite strong. Moreover, it is now a standard practice everywhere to embed biometric identification in KYC systems. Blockchain Technology, alongside Biometric IDV, builds a strong foundation for a robust eKYC. Thus, customer identification & verification becomes swift, error-free, and spoofing proof.
Final Thoughts
Biometric Identity Verification Systems help in the mitigation of Financial Crimes like money laundering & terrorism financing. In the view of regulators, biometric verification is by far one of the best approaches for securing financial transactions. They help in regulating the financial system through ongoing monitoring and detecting suspicious activities. As the financial world is advancing and rapidly digitizing, the fight against financial crimes is also evolving to harness the power of technology, data analytics, and global cooperation to safeguard the integrity of the global financial system.
Also Read: The Role of AI-powered ID Verification in Combating Digital Fraud
Table of Contents
- Introduction to Biometric Identity Verification System
- Evolution of Biometric Identity Verification System
- Types of Biometric Identity Verification System
- Use cases of Biometric IDV System.
- Challenges in Implementing Biometric IDV Systems
- Robust KYC through Biometric Identity Verification System
- Final Thoughts





