What is Liveness Detection?
Liveness Detection is an Identification and Verification technique that technically differentiates between a fake identity and a live individual. It is by far one of the most sophisticated ways of protecting digital identities and the most preferred way of securing financial systems. KYC (Know Your Customer) tool providers largely rely on liveness detection for robust customer onboarding.
History of Liveness Detection
The concept of liveness dates back to 1950 when Alan Turing introduced the “Turing Test” which measured a computer’s ability to act like a human. Liveness Detection is derived from this concept that measures the Artificial Intelligence (AI) ability of a computer to interact with a live human accurately. In simple words, Liveness Detection is verifying that the person accessing the computer is a real and live person. Moreover, Ms. Dorothy E. Denning was the first one to coin the term “Liveness” in her Magazine Article entitled “Its Liveness not Secrecy that Counts.”
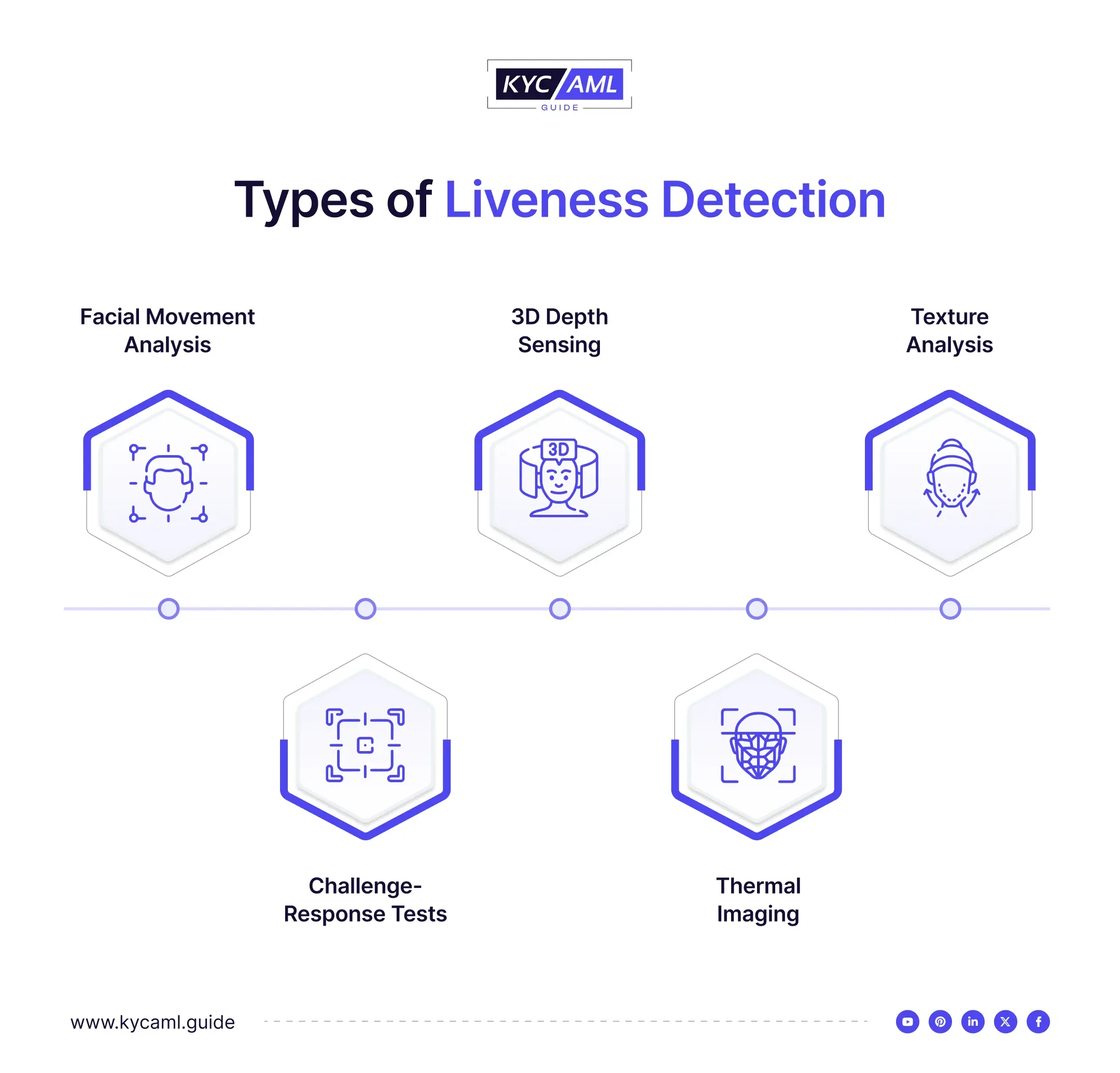
What are the Types of Liveness Detection?
Several types of Liveness Detection are used under different scenarios to detect an identity.
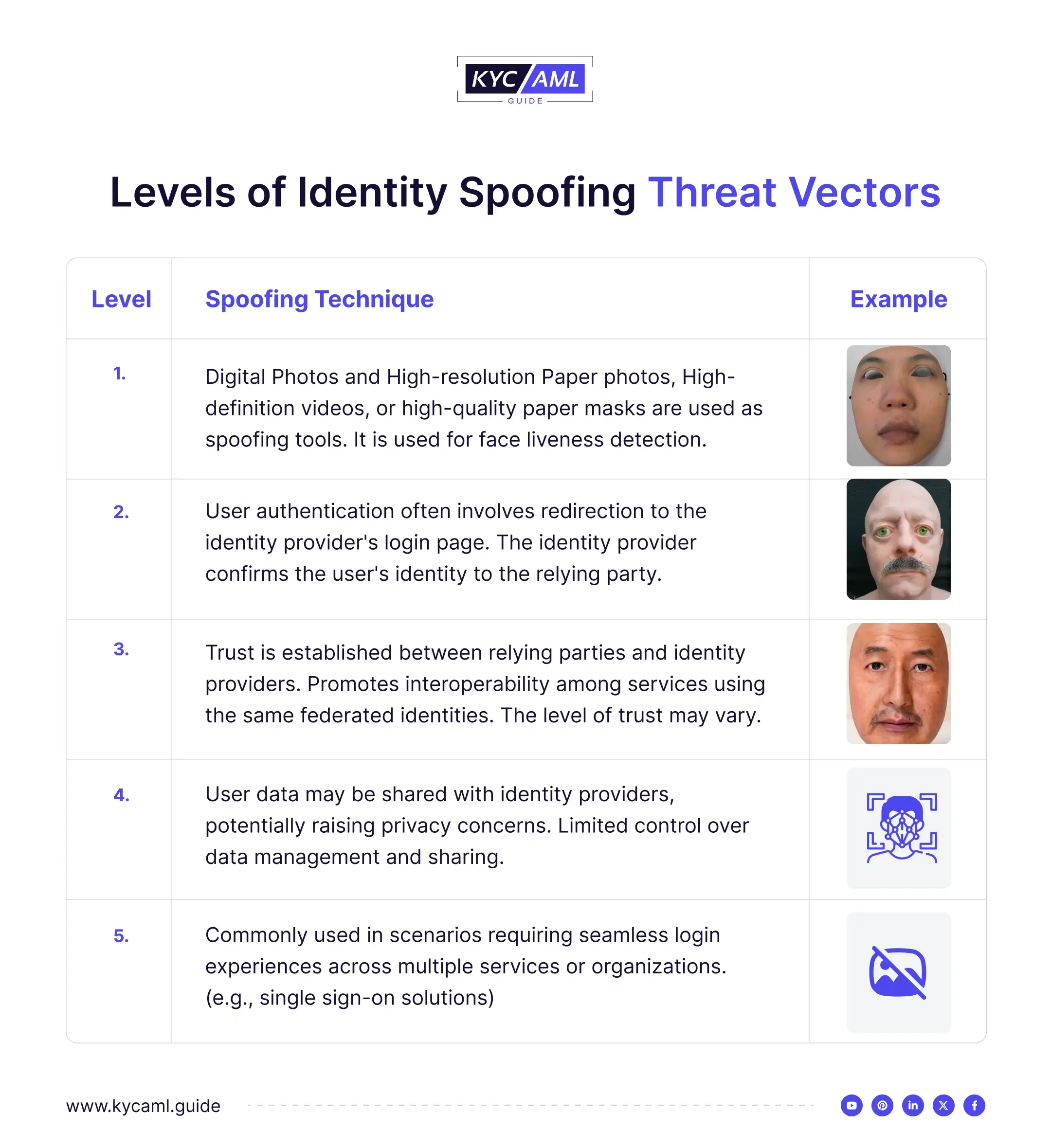
Levels of Identity Spoofing Threat Vectors
Whenever a non-living object or an imitation of a human is brought in front of a camera or a biometric sensor, it is an attempt to identity spoof. Different objects are used by scammers including Photos, Videos, Masks, and face dolls to spoof. Here are the 5 main levels of bypassing a liveness detection technology.
How has AI made Liveness Detection Difficult?
Artificial Intelligence was first introduced to facilitate many industries. But since the technology got into the hands of criminals, they have exploited AI for illicit gains. One of the major ways in which Liveness Detection has been compromised is Identity Spoofing through Gen AI images, videos, and other methods of spoofing. Following are the main ways in which Artificial Intelligence has been used as a tool for Identity Spoofing:
1 Deepfakes
AI has enabled almost everyone to create a highly realistic video, image, or voice of a person that doesn’t exist. AI Deep Fakes are also made for celebrities to use their identity for scamming and committing other crimes. Deepfakes are by far the biggest identity spoofing risk to the digital identity verification system.
For example, Brad Garlinlghouse, CEO of Ripple’s Deepfake recently used to commit a giveaway scam.
2 Adversarial Attacks
Adversarial attacks are mostly AI-driven and look for loopholes in the Identity Verification system and attempt to bypass liveness detection by generating deceptive features closer to live behaviors.
3 Generative AI Modeling
It is the main technique that has allowed Spoofing Attackers to continuously improve the quality of AI-Generated identities. This has made liveness detection challenging.
4 Auto Replay Attacks
Replay attacks are a type of Presentation attack in which identity spoofing is done through stolen files that are replayed over and over again to outwit a biometric identification device. Attackers/Spoofers use the stolen voice of an individual to retain the liveness and use it to illegally access their accounts.
Also Read: How to Detect Identity Spoofing?
How Liveness Detection Works?
Liveness Detection eliminates the Identity Spoofing threat during the Identity Verification process. Algorithms are used to detect spoofed images involving neural networks that act just like a human brain trained through machine learning. Generally, Liveness detection requires different trained algorithms to be integrated with the auto-capture components. Users can take selfies through mobile cameras and Liveness Detection through KYC Tools detects spoofed identities to protect genuine users.
It accurately detects different types of presentation attack vectors that use:
- Screen Attacks
- Print Attacks
- 2D mask Attacks
- 3D mask Attacks
Main Things to Consider in Liveness Detection
While using a liveness detection program, a user must know the following things to properly use the technology and avoid hassle in remote online onboarding.
- Understand the liveness detection technology such as facial recognition liveness detection, depth sensing, or biometrics liveness detection.
- Always ensure that the liveness detection technology is adaptable to the latest and evolving spoofing attacks such as presentation attacks using deepfakes.
- The Liveness Detection tool should provide user-friendly guidelines during the onboarding process and every time a customer attempts to sign in. This will help them submit optimal images in less time with minimum effort.
- For enhanced security consider multi-factor biometric authentication enhanced with measures like facial features, heat sensors, and blood flow recognition.
- False positives are a main concern in Liveness detection and Identity verification. The system can falsely flag a genuine user’s log-in attempt as a spoof attack.
- Always evaluate the privacy and data security element of the Liveness Detection program that ensures the safety of your biometric data and its proper storage.
- KYC Vendor Reputation is an important factor that users need to consider. The track record of Identity Solution in providing Liveness Detection is important including customer feedback, reviews, and industry recognition.
Also Read: FAR vs FRR
How KYC AML Guide help KYC Solutions in enhancing their Liveness Detection?
KYC AML Guide’s Vendor Analysis is a comprehensive and well-documented guidance path for KYC Tools that has analyzed and compared the Liveness Detection systems of top-tier KYC Solutions in the market. Ensuring a robust liveness detection to detect spoofing attempts through deep fakes is essential for maintaining a KYC tool’s reputation in the market.
Visit us for more information.





