What is Transaction Laundering?
When an authorized customer performs a payment card transaction on behalf of a legitimate company unknown to the merchant or payment service provider (PSP), transaction laundering occurs. EverCompliant, a privacy and risk management company, estimates that criminals laundered $352 billion through e-commerce channels worldwide in 2016. This amount is greater than Denmark’s whole GDP!
This is a significant blind spot for traditional banks because transaction laundering is outside the reach of the established transaction monitoring system. Furthermore, payment firms face a costly and time-consuming difficulty due to the speed and sophistication of transaction laundering.
Transaction Laundering is described using terminology such as unauthorized aggregation, undisclosed aggregation, and factoring. This is because unlawful payments from several websites or aggregators are combined and processed via the same legitimate business account. Aggregation, on the other hand, is a valid payment method that small business owners utilize to collect credit and debit card payments from their clients. As a result, the phrase “Transaction Laundering” has evolved to signify the conversion of financial transactions into money laundering.
To collect their illicit funds and re-enter the financial system, transactional money launderers frequently employ one or more ways. This includes the establishment of shell businesses, front companies, pass-through companies, or funnel accounts
The ultimate punishment is taken by the MSP of a merchant who acts in money laundering, whether deliberately or unknowingly. The regulation requires MSPs to authenticate their customers’ legal identities and identify the entity’s ultimate beneficial owner (UBO). Traditional Know Your Customer (KYC) continues to focus physical qualities of a legal business rather than digital aspects, making the payments sector particularly vulnerable to transaction laundering.
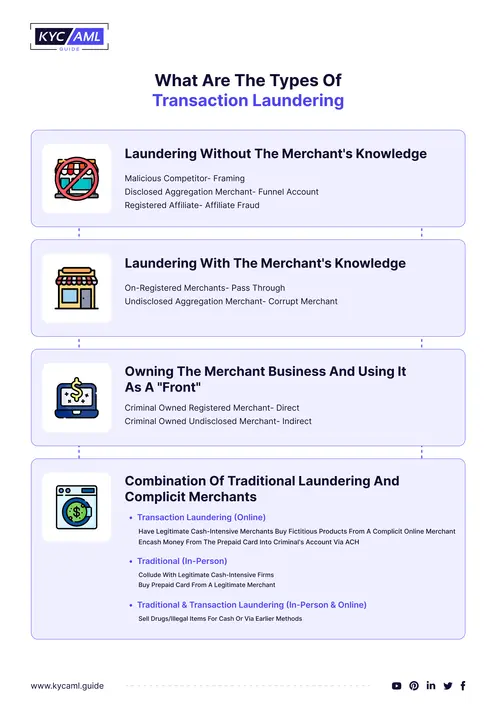
Types of Transactional Laundering
There are many ways to do transactional laundering but some of the most common types are
1. Mail or Telephone Order (MOTO):
Website operators attempt to process payment for the requested product or service offline. This can be accomplished via phone, link, or other means unrelated to the webpage. Transaction launderers can obtain sensitive credit card information and perform transactions to conceal the destination of funds.
2. Payment Page Redirect:
When a customer attempts to purchase a product or service, they are redirected from the main website to another URL to complete the transaction. This strategy enables the transaction launderer to conceal the source of the cash coming from the front page, fooling the bank or third-party payment service provider (TPPP) into thinking it is processing payment for another organization. VPNs are also useful for this type of transaction laundering.
3. Affiliated Businesses:
The front will process transactions via a website in the same or a comparable industry. The affiliate utilizes your credentials as a merchant, deliberately or unknowingly, to process online payments for the transaction launderer, receiving a share of the sale. Transactional money launderers might conceal the true origin of cash by tricking customers or the affiliate website. This also makes affiliate sites involved in money laundering activities.
4. Multiple Processor Laundering:
Several credit card payment alternatives listed under multiple customer names are used by front-site operators. Transaction launderers make it tough to track where money is moving and invent numerous ways to obtain it. A malevolent actor keeps accounts at multiple financial institutions to avoid accusations of corrupt activity.
Regulations About Transaction Laundering
Traditional money laundering measures and rules by regulators are insufficient. Regulators have the authority to levy significant fines on banks and payment service providers for transaction laundering. While FinCEN is actively implementing different protections to combat commercial fraud, EU law has addressed this issue through 4AMLD and 5AMLD. Despite the US Treasury’s Financial Crimes Enforcement Network (FinCEN) and stricter money-laundering legislation than other governments, implementation methods focus on traditional commercial and financial services such as banking, capital markets, insurance, and cash deposits.FINCEN penalized Merchants Bank of California $7 million in 2018 for AML offenses in transaction laundering.
How Does it Work?
Traditional money laundering has grown in popularity as a result of criminals’ ability to develop or buy legitimate websites and utilize them to obtain merchant payment accounts. The valid account’s payment gateway is also used to restrict illegitimate transactions and PSP.
Also known as electronic money laundering or cyberlaundering, transaction laundering has become popular because of the ease with which criminals can set up legitimate-looking websites or gain access to legitimate websites and use those to access genuine merchant payment accounts. Illegal transactions are then routed through the payment gateway of that real account and laundered unknowingly by the payment service provider (PSP).
The transaction laundering process involves the following steps:
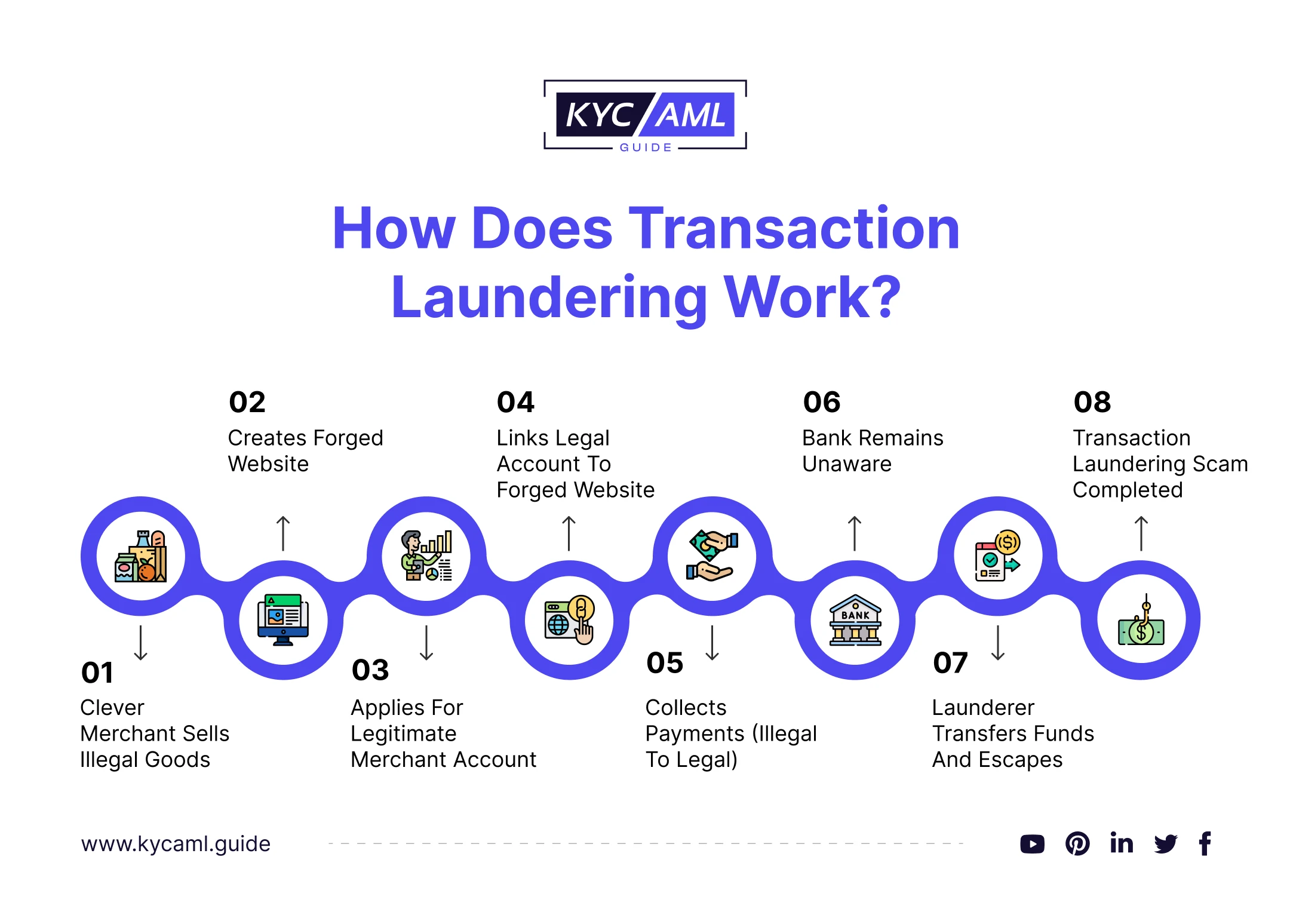
- A criminal, posing as a legitimate consumer, builds an unlawful website where customers can sell illegal goods.
- Criminal route card payment using this website via another legitimate merchant’s PSP account.
- The payment is processed by the PSP, who then calls the receiving bank for funds.
- The laundered money is held in the criminal’s bank account.
- Although a criminal may use his own website to sell narcotics, weapons, or other illegal items, a merchant website used by a criminal to conduct his business does not sell unlawful products, such as clothes or books, to aid the sale. A legitimate merchant website could be involved in a criminal’s money laundering plan or founded by a criminal, or it could have been compromised.
How is Smurfing Linked to Transaction Laundering?
Smurfing is a method of money laundering where large financial transactions are divided up into smaller, less suspicious amounts to avoid being noticed. In the broader context of transactional laundering, this technique is applied. The goal of transaction laundering is to mask the true nature of transactions, frequently by processing them through accounts or businesses that appear to be legitimate. In order to divert illegal funds through the financial system without raising any red flags of money laundering, smurfing is one of the strategies that can be used in transaction laundering schemes.
Why is Transaction Laundering Difficult to Detect?
Although this method of money laundering appears simple, it is difficult to detect transaction laundering for the following reasons:
1. Payment Chain Complexity:
The payment process, which includes shopping carts, payment gateways, payment service providers, and banks, can take numerous forms, and payment is made through multiple channels, with the individuals paying. This makes distinguishing between legitimate and illicit transactions difficult.
2. Inability To Protect Websites:
Some customers may be unaware that their website is being used for illicit purposes via affiliate programs or as a side website.
3. Several Unreported Websites:
Transaction breaches can occur via hidden websites that the bank is unaware of and hence cannot monitor. Unreported websites are ignored by traditional surveillance systems.
4. Growing Use of Corporate Credit Cards
Virtual card numbers, business cards, and prepaid cards, unlike credit or debit cards, are not tied to the user’s identity. A fraudster can use stolen card details to conduct a range of fraudulent transactions.
How to prevent Transaction Laundering?
Suspicious activity is defined by FinCEN as any transaction that does not fulfill a business or lawful purpose. It further states that transactions for which there is no reasonable explanation can be classed as suspicious activity. Activities such as money laundering, cash transaction structuring, check fraud, check kiting, wire transfer fraud, mortgage and consumer loan fraud, misuse of position (self-dealing), identity theft, and terrorist financing are some activities put under surveillance as suspicious transactions.
Companies can prevent transaction laundering threats by doing the following:
- Inspect the suspected seller’s website.
- The amount of transactions should be compared to the content of the suspicious website.
- Products sold on the suspect website should be compared to projected sales.
- KYC and AML procedures are critical for detecting and preventing transaction laundering by verifying the identities and sources of funds involved in financial transactions, conducting thorough due diligence on business partners, monitoring financial transactions for suspicious activity, and staying informed about emerging risks and trends in the financial industry.
- Perform customer due diligence.
- The use of modern technologies and AI for prevention and early detection
Bottom Line
Regulators and governments all around the world are enacting new laws to combat transaction laundering, while criminals are inventing new ways to conduct crimes. This creates an intriguing struggle between the two. Various countries and regulatory authorities have devised and implemented anti-money laundering (AML) legislation to fight this threat.





