Financial Fraud has taken many shapes over time. Account Takeover Fraud or ATO Fraud is a type of Identity Theft Fraud where a malicious person actually ‘takes over’ an operational online account of some sort. The online account can be a bank account, social media profile, or even an email address. Customers while leaving traces and trails in online activities give a chance to the fraudsters to take advantage of such vulnerabilities.
Few Projections related to ATO Fraud in 2023 (Aite Group)
- By 2023, the projected losses due to Identity Theft will amount to a staggering $635 billion.
- Every 1 out of 5 Adults in the US is a victim of an ATO Fraud Attack.
- Losses due to Account Takeover Fraud Attacks in the US are averaging $12,000 for every victim.
- In 2021, the European Payments Council found the highest spike in ATO Fraud Attacks of 280% that were COVID-related frauds.
- Phishing websites also surged and frauds increased by 250%.
These statistics show rising concern about increased Identity Fraud Attacks in the US and beyond.
Account Takeover Fraud is initially seemingly harmless. Since fraudsters gain full access and control of an account, they can change the credentials or even use the account for criminal activities. In the case of bank accounts, a fraudster can use the victim’s account for money laundering or depositing terrorism funding money. Similarly, there are multiple criminal use cases where ATO Fraud facilitates financial crimes.
4 Stages of ATO Fraud Attacks:

Stage-1:
Data Breaches is the first stage of ATO Fraud where cyber criminals gather data and information about the user’s account. Various methods are used for Data breaching including:
- Social Engineering
- Credential Stuffing
- Phishing
- Malware & Keyloggers
The main objective of attackers is to obtain the information that can get them into the account such as passwords, usernames, security patterns & passcodes. In the case of biometric security, one can go deep and even obtain fingerprints, etc.
Stage-2:
Creating Lists: Once, the required information has been obtained [data is breached], the combo lists are created. These lists are compiled forms of data of usernames, and passwords that are obtained through multiple data breaches.
Stage-3:
While implementing the attack the fraudster is already halfway through. All they need is to log in to the victim’s account and change the credentials without the victim being notified.
Stage-4:
Once the credentials have been changed, the account is in complete control of the Fraudster. This is why it is known as ‘Account Takeover Identity Theft’. It is much more difficult to detect ATO Fraud as compared to Credit Card fraud.
Why ATO Fraud is difficult to catch?
Account Identity Theft is hard to catch because of the nature of fraud. Once fraudsters gain control of an account, the first thing they do is change all the credentials and other information. Also, it is done in such a way that the real owner of the account will not be notified. A study by Javelin Strategy revealed that it takes at least 16 hours and costs a little less than $300 to resolve an ATO Identity Theft.
Another main reason for the difficulty in ATO Fraud Detection is the same use of passwords in different accounts. When the same password is used for multiple accounts, fraudsters can easily gain access to multiple accounts at the same time. This gives access to fraudsters to forge different and new accounts from your existing bio data and then commit financial crimes and frauds even more. And the worst part is you can be held accountable for all this mess.
Account Takeover Identity Theft is becoming more common as social media platforms and other applications enable users to gain access via different options such as Google Sign In or Facebook Sign In.
The rising trend of ATO Fraud
Another report by Javelin follows some recent trends in ATO Fraud becoming common.
- ATO Fraud increased by a staggering 282% between 2019 – 2020.
- ATO Identity Theft Attacks have increased by 64% for Financial Institutions after the COVID-19 pandemic.
- Each year Account Takeover Fraud losses amount between $ 5 billion to $ 25 billion.
Also, Read the Anti-Fraud Management in MSB
Major Types of ATO Fraud
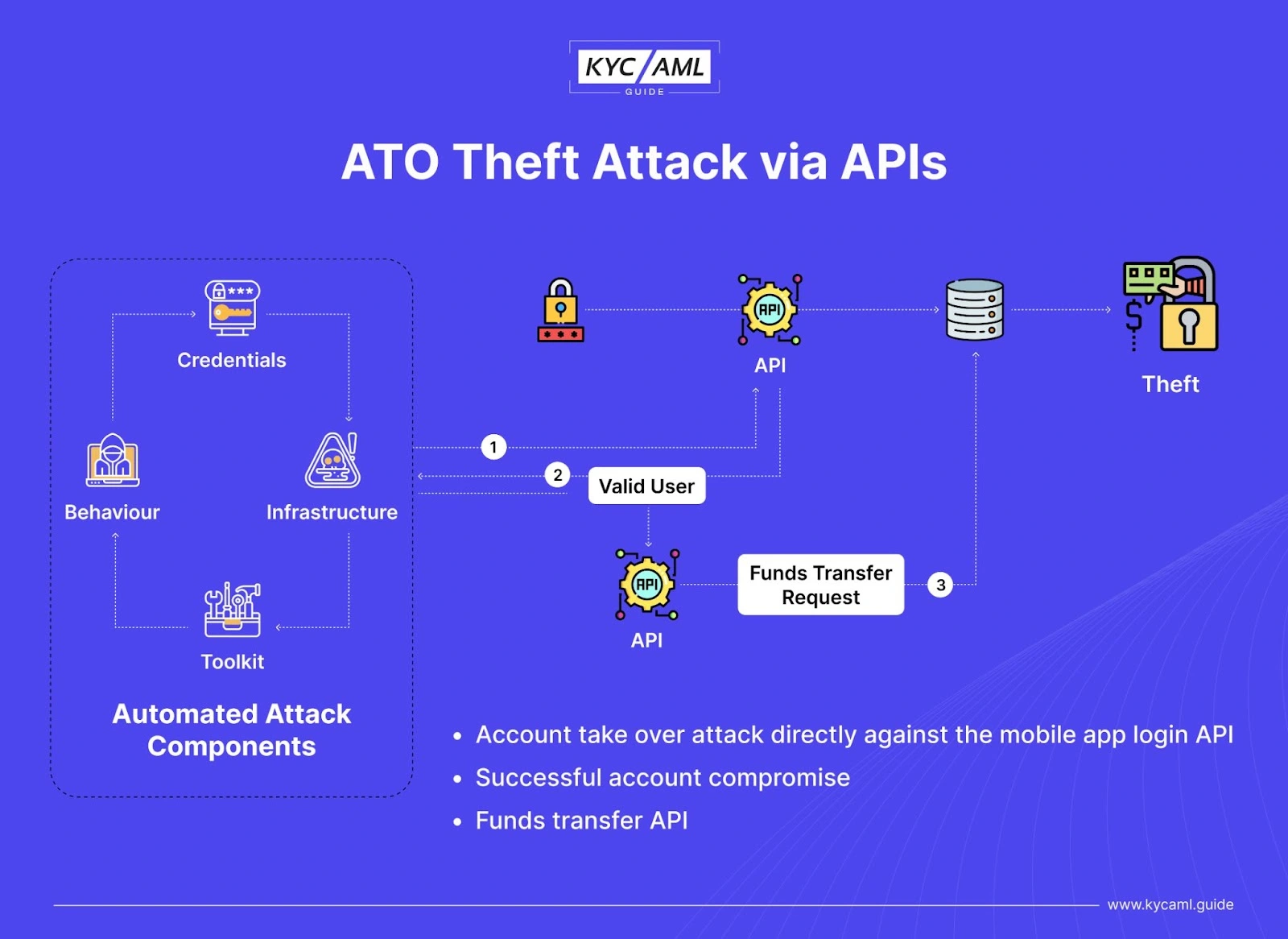
Account Takeover Fraud through APIs
Usually, an Application Programming Interface has a built-in security system against fraud attacks. But as fraud techniques are advancing, there are more cases of bypassing API security in different scenarios. Following is a diagrammatic explanation of how an ATO Fraud Attack is carried out while bypassing the APIs.
ATO Fraud through Phishing
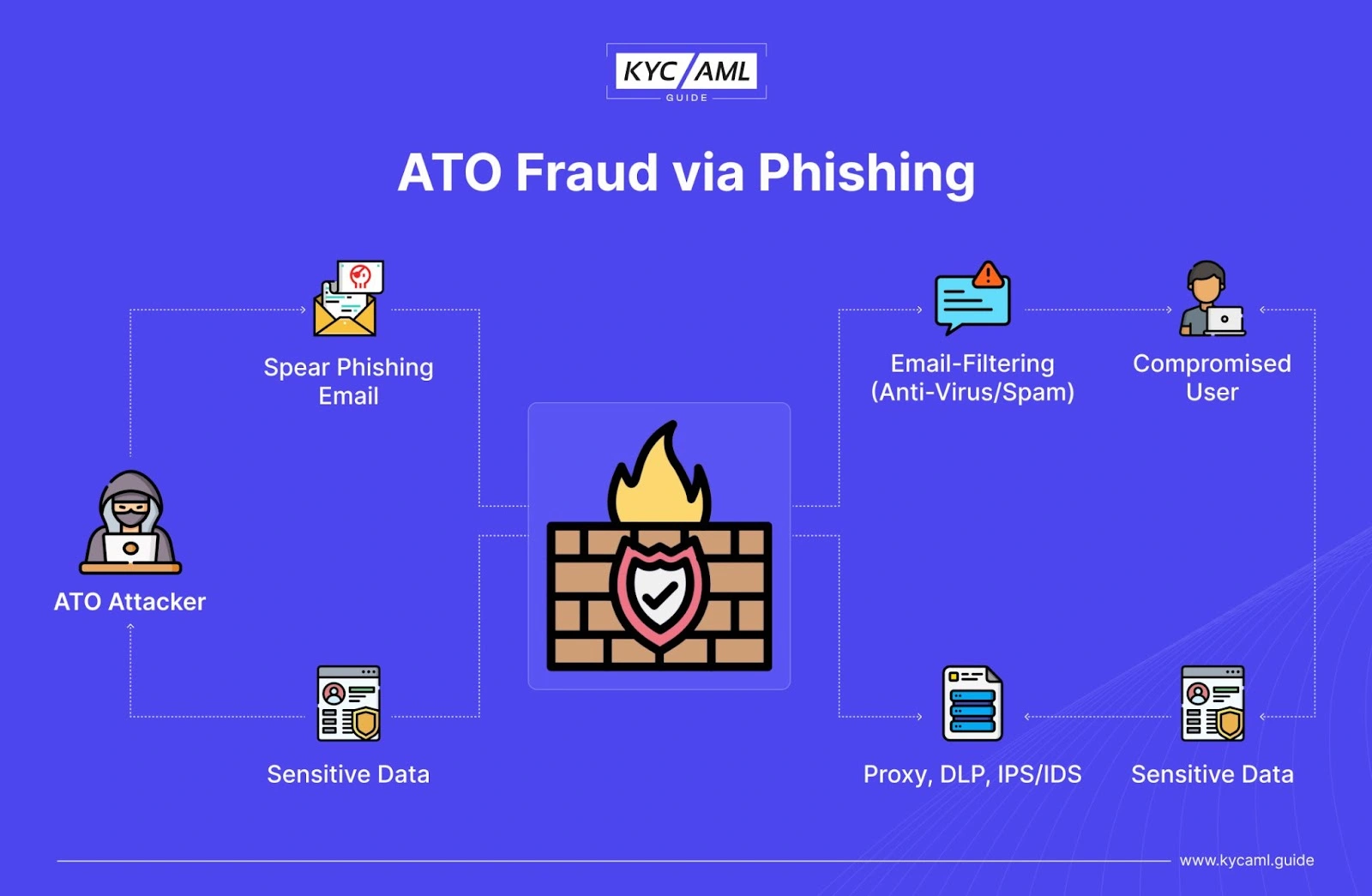
In the above image, you can see that an ATO attacker is focused on gaining access to the sensitive personal information of a certain account. For this purpose, he tries to bypass the firewall and other security barriers online. For this purpose, they might use multiple types of phishing including the following:
- Phishing emails: The most common type of phishing is via emails. Fake emails are sent to the user’s inbox which may not be filtered as spam sometimes. Once a user is intimidated by the fake offer or other fraudulent technique in, he or she might provide the credentials by logging in, registering, or other forms through the provided link. Phishing emails are also known as ATO scam emails.
- SMS Phishing (Smishing): We commonly see people receive SMS messages having offers, lucky draw winning messages, or other game shows and even lottery winning messages. Beware! As it is all fake. Never trust such a message and block every unknown number that seems suspicious. You can report such SMS to law enforcement as well
- Voice Phishing (Vishing): Since AI (Artificial Intelligence) has revolutionized voice recognition, fraudsters use it for their benefit. By having call recordings, Voice notes, and other forms of the voice of the victims or target, they are now able to generate complete and undetectable voice notes and messages. They can even use the stolen Voice for fake calls for extortion and take sensitive user information from relatives by faking the ID over phone calls.
- Malicious Website Links: ATO Fraud can also occur through fake websites that may seem legitimate. Users while subscribing to them provide their credentials and hence become fraud victims. These links are often sent through emails combining these two types of phishing.
- Social Media Phishing (SM Phishing): Facebook, Twitter, and other social media platforms are now used to trick people through fake accounts and other techniques. Social Media phishing is currently rising at a haunting pace.
- Instant Messaging and Chatting: During chatting and instant messaging, you need to stay alert to these pop-up messages, fake offers, and any other tricks that fraudsters might use as bait.
Apart from these main types of ATO Fraud, there are other methods to carry out an ATO Attack.
- Brute Force Attack: Using random credentials through a bot network making numerous login attempts on an hourly basis.
- Malware Attacks: Commonly, keyloggers are used by attackers to steal personal data.
ATO Fraud Prevention – A Handy Guide
Preventing Fraud is an ongoing activity that requires regular updates and adopting new and stronger preventive measures. It has been seen that people who surf the internet ethically and do not explore unnecessary things are much safer. But still, there is an imminent threat of ATO Fraud that is rising every passing day. Here are a few basic steps to protect yourself from ATO Fraud and you can apply them right away without spending any extra money.
1. Apply the strongest password
Google mostly suggests the strongest passwords for securing your accounts. What you need to do is choose a combination of Capital Letters, Small Letters, irregular words, numbers, and special characters. You can change it every two months. In this way, cracking the password will become difficult for the fraudsters. But always remember to retain this password secretly somewhere like a piece of paper or a notebook which is kept safe somewhere only you know.
2. Apply Multi-Factor Authentication
Adding the second tier/layer of security to your Authentication process is always a best practice. Always use multi-factor authentication that will require biometric authentication, Identity verification, and maybe a security question too.
For example, in banking applications, you will enter the password and your username. Right after that, you can enable the biometric and it will ask you for your chosen verification method. This method can be facial recognition through a mobile camera, thumb impression, or ID card verification.
3. Limiting the sign-in attempts and period
You can set a time limit of 5 to 20 seconds in which the application will prompt the person to enter the correct password and other details. Also, you can limit the number of tries/attempts to log in to a standard number of 3 attempts.
4. Getting notified of changes and login attempts
It is a standard practice to protect yourself against Account Takeover Attacks so you can set notifications for each login attempt to your phone or device. In this way, you can block any unknown login attempt and protect yourself from ATO fraud.
Role of KYC and AML in ATO Fraud Prevention
KYC (Know Your Customer) and AML (Anti-Money Laundering), are of great importance when it comes to ATO Fraud. Since Account Takeover Identity Theft gives complete control of an account to a fraudster, he can now use it for Money Laundering and other crimes. Ultimately, the solution against it is a robust KYC AML system. A perfect KYC and AML system covers all aspects of financial security including online and account security.
Final Thoughts
ATO Fraud is one of the most damaging and irritating types of fraud. Online account security in every service is compromised due to the rising concern of ATO Identity Theft. To mitigate this, one needs to have proper information, training, and guidelines on how to combat fraud at an individual and customer level. Moreover, implementing a robust compliance system for KYC/AML and Anti-Fraud Management is now a need of time.
Visit the KYC/AML Guide for more informative articles.





