What is a Fake ID?
A fake Identity is defined as a fabricated persona and personal information deliberately created to deceive and mislead others. It includes false names, dates of birth, addresses, and any other details that can be forged. Fake Identity documents are created to spoof a genuine identity or create a new identity that only exists in papers. This fake identity is used to commit different crimes like hacking, online scams, money laundering, and fraud.
How Dangerous is a Fake Identity?
Fake Identity poses a serious threat to society as a whole. Fraudsters can steal millions of dollars and even steal sensitive information and sell it to terrorists leaving no trail of information as their identity was fake. National Security agencies and regulators consider fake identities as a serious crime.
What are the main types of Fake IDs?
There are 5 main types of fake identities:
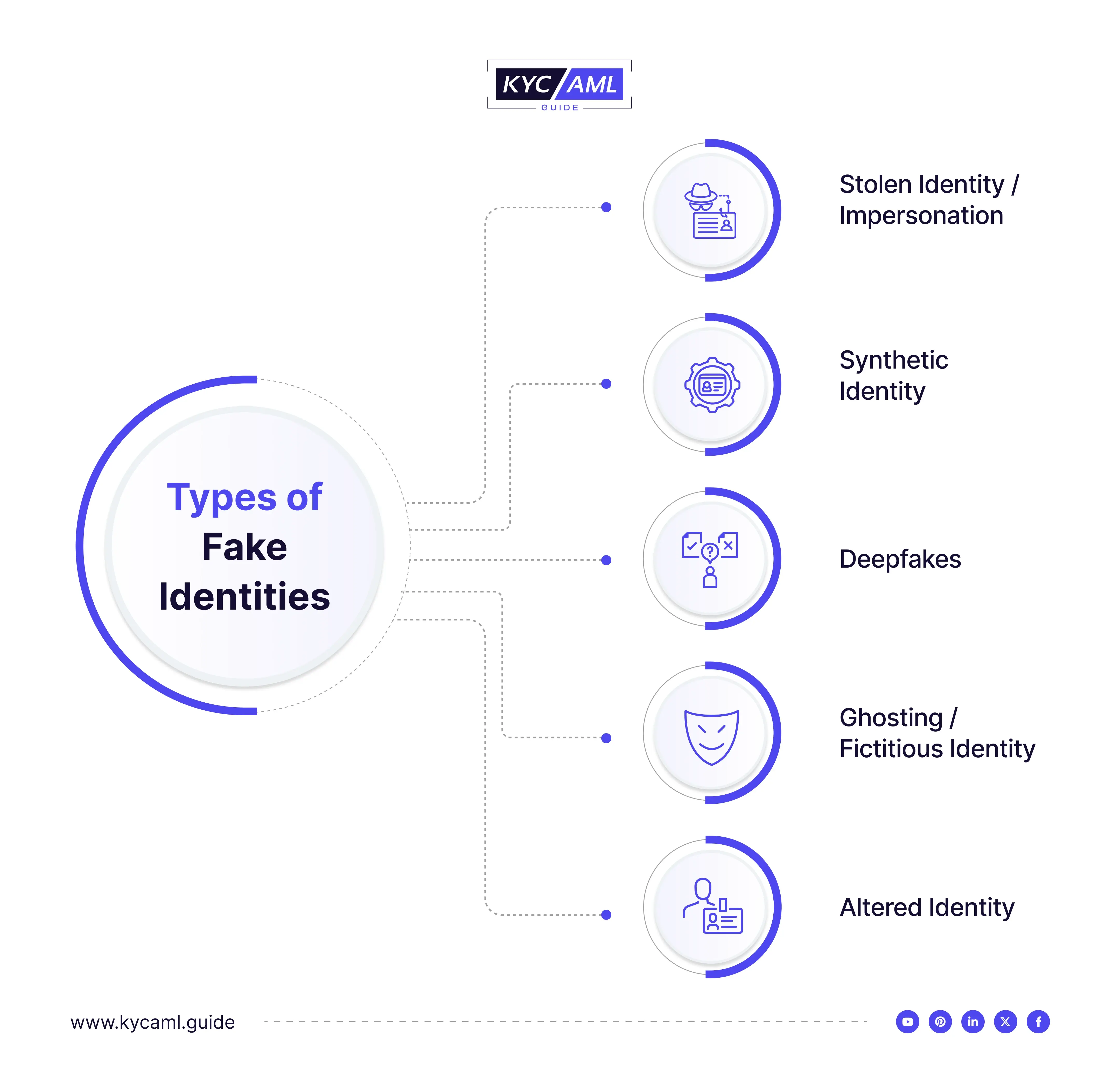
| 1 | Stolen Identity/ Impersonation | It involves the misuse of the identity of real individuals without their consent. It includes imitating someone who has real and valid identity credentials for illicit purposes. It is typically obtained through identity theft. |
| 2 | Synthetic Identity | Synthetic Identity is made by combining real identifiable information with fake details. For example a real name with a fake date of birth and address. |
| 3 | Deepfakes | The illegal use of Artificial Intelligence (AI) creates realistic but entirely fake audio, video, images, or even text documents. It has taken identity fraud to a whole new level. |
| 4 | Ghosting/ Fictitious Identity | It uses entirely fake and fictitious details where the identity does not correspond to any real person. It is most commonly used in online platforms where no identity verification checks are performed. It is also called ghosting in which an entirely new identity by fabricating all the necessary details. This is often done to escape legal issues or to start afresh without a trace of the previous identity. |
| 5 | Altered Identity | It uses modification techniques of one’s own identity, for example, changing a driver’s license details, photo, etc. |
Identity Fraud Statistics 2023
Two reports on Identity Fraud were recently released that highlight concerning statistics in 2023. An overview of both reports is given below accordingly:
2023 Identity Theft Facts and Statistics (US)
According to the National Council on Identity Theft Protection’s report,
|
|
|
|
|
ENISA’s post-COVID-19 Workshop on Remote Identity Proofing
This workshop was held in July 2021 by the European Union Agency for Cybersecurity and analyzed different fraud scenarios, remote identification methods, and countermeasures in this regard.
Identity Fraud Report 2024
According to this report:
|
|
|
|
Tips to Detect Fake ID
Detection of Fake IDs is highly important for the prevention of any type of Identity Fraud. To properly exercise Anti-Fraud management against identity fraud techniques, here are some steps that anyone can take to verify an identity.
- Compare the uploaded image of the ID document or photo with the live one.
- Genuine Identities are made with a high-quality polycarbonate material that is different from cheap plastic material. You can feel the material in your hands and an expert eye can tell the difference easily.
- Look for the Ghost Image in the identity document that most Fake ID users miss out on while forging the document. It is a semi-translucent image in the identity usually seen on either side of the document.
- Check the holograms of the identity document as they are difficult to copy.
- Laser perforation can help detect a Fake identity by passing a light through the ID Document. If the light passes through the ID document in the required direction, it is an authentic ID otherwise suspect it and report it.
- You can also look for missing microprinting like name under the photograph, date of expiry, etc.
- Fine line patterns also differentiate the original ID from a fake one.
How to Professionally Detect ID Fraud?
With the rising number of identity fraud, government-issued Identities are also being stressed to prevent the risks of crimes through fraud. Here are the three main ways in which KYC Identity Verification Solutions professionally detect a possible Identity Fraud activity.
Data Analytics
- This technique employs MRZ (Machine Readable Zone) to verify the identity’s authenticity. The original Identity template is used to check the data validity present in the ID document. For example, a UK driver’s license (as shown) has an MRZ code at the bottom of it.

This code has all the identity information present on the identity document. So, if an identity is fake, its MRZ code will show wrong or no information on the MRZ reading machine.
- Algorithms use specific rules in the form of mathematical calculations to identify anomalies and flaws in an Identity. These rules are strict to follow when an identity is issued. For example, a PAN Card has the first 3 characters as alphabets between A to Z, the fourth character shows the type of the cardholder, and 5th character is the first letter of the last name of the cardholder.
- NFC (Near Field Communication) Chips enable communication between 2 devices placed at short range. Additional verifiable information that is only readable by those devices on both ends. The information is matched from sender to receiver and compared for any discrepancies or mismatches to detect fakeness.
Visual Document Authenticity
- Comparing the document templates that are government-issued with those that an identity holder carries is the first step where most fake identities are detected.
- Digital Tampering trails can be detected by professional anti-fraud techniques where sophisticated technologies are employed to detect any tampering in an Identity document under review.
- A KYC Document Verification Software is also capable of detecting font anomalies that are left by fraudsters while forging a Fake ID.
- Digital signatures, watermarks, and other security features are also a good way of detecting fake identities.
Apart from this, the proof of ownership of an identity can also be checked by a KYC Verification Tool. it uses biometrics facial recognition or a selfie picture to match the identity document which helps in verifying the true person’s identity.
KYC Solution Providers in Curbing Identity Fraud
KYC Solution providers need to scale their identity verification capabilities according to the sensitivity of their client’s business. For this purpose, they are required to follow the standardized guidelines provided by regulatory bodies in scaling an Identity Verification solution.
But keeping up with the ever-changing regulatory landscape is another challenge for both the clients and the KYC Vendors.
So to mitigate this, KYC AML Guide offers KYC Technology Buying Consultancy, Vendor Analysis, and other associated services to help organizations prevent identity fraud through enhanced identity verification.





