What is Morphing?
Morphing is a sophisticated graphical technique that involves seamlessly blending or transforming two or more images to create a fluid transition between them. This process utilizes animation and image manipulation to merge the characteristics of the input images to generate entirely new images. Morphing Images allow for the creation of visually dynamic sequences where the boundaries between the original images become imperceptible. This makes morphed images look realistic and deceives ordinary people.
Uses of Morphing
Morphing has both positive and negative uses. Morphing is used in both positive and negative terms here is a brief chart of its different applications:
| Positive Uses | Negative Uses |
Entertainment and Media
|
Impersonation / Identity Theft
|
Biomedical Imaging
|
False Evidence
|
Face Aging
|
Cyberbullying
|
Forensic Reconstruction
|
Deep Fakes
|
Virtual Try-on
|
Fraud
|
Types of Morphing
Facial Morphing is the most common technique of a morphing attack which is used to hurt a person’s reputation online. Here are the 3 main types of Morphing:
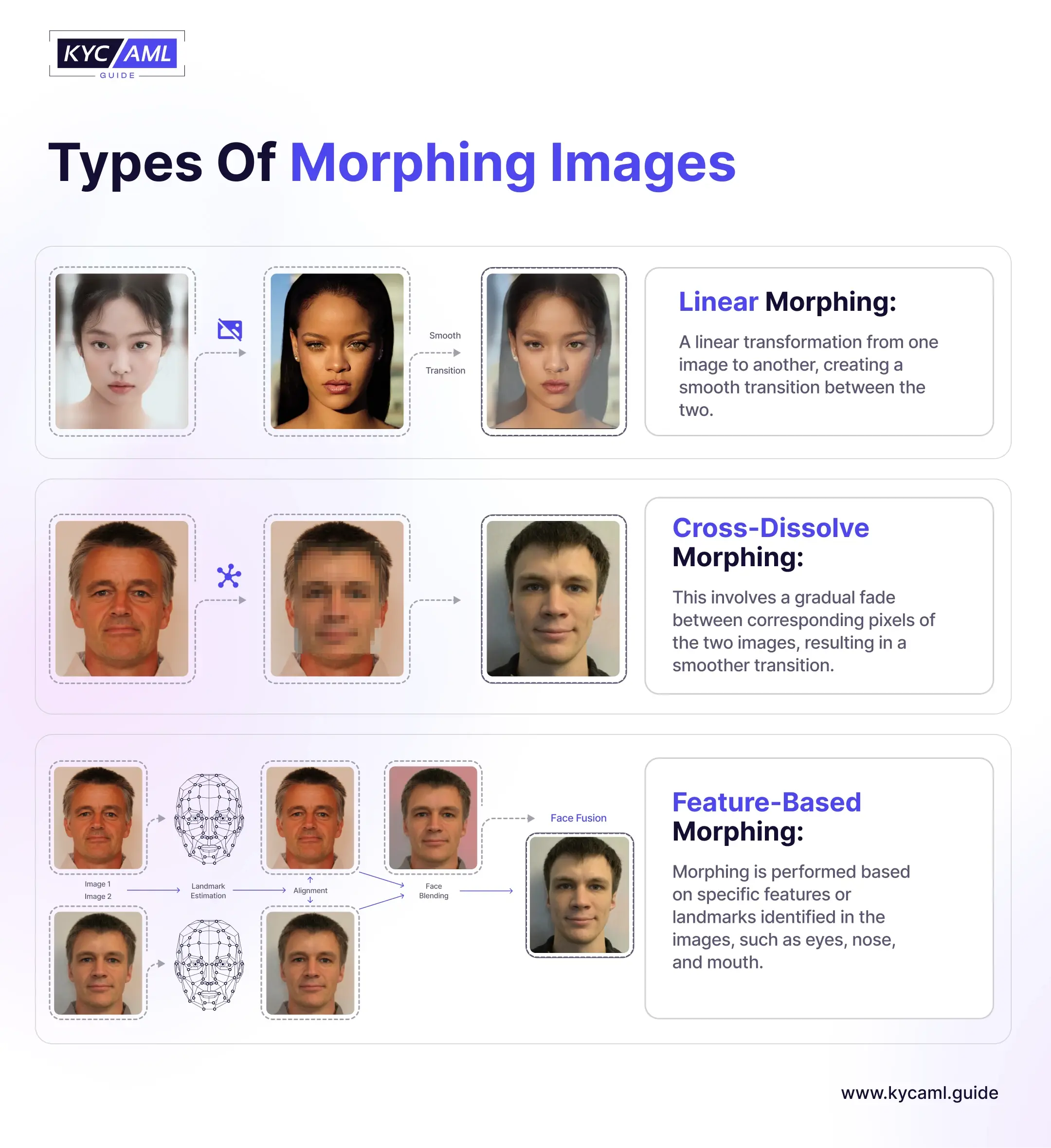
1) Linear Morphing
It refers to the linear transition between the source and target images. Two completely distinct images are merged in animation style. It is comparatively easier to detect linear morphing.
2) Cross-Dissolve Morphing
It involves a gradual and high-definition fading technique of the pixels of two images that results in a much smoother transition as compared to linear morphing. It is quite difficult for the human eye to detect Cross-Dissolve Morphing.
3) Feature-Based Morphing
In this type of morphing, the facial landmarks (eyes, nose, and lips) are used for image transition with subtlety and higher accuracy. It is by far the most sophisticated morphing technique.
How Does Facial Morphing Work?
Morphing faces requires the blending of two images in a sophisticated and undetectable way. Usually, a face blender application software is used to blend the two distinct images and create an entirely new and realistic image.
There are 5 main steps to create a morphed image through a face blender.
1) Adding a Morph Node
In the first step, two source images or clips and the output node are decided in a morphing application software.
2) Creating the Source Shape
Usually, masking techniques and tools like the ‘spline tool’ are used to create the source shape. Since it is a highly sophisticated and intelligent tool, it does not require the user to select and draw the exact source shape. Minor inaccuracies are automatically corrected by the software through AI (Artificial Intelligence).
3) Creating the Target Shape
The same process is repeated at the target node but with predictions and accurate results. Users can graphically guide the system to create the target shape during morphing.
4) Adding a Correspondence
The system adds a correspondence between the source images and uses advanced image-blending techniques to mix and match the images. It is done by selecting the source images and matching them with the landmarks (eyes, nose, and lips) of the target image.
5) Blending and Animating the Final Output
Finally, the output image is created with adjustments and intelligently removing any inconsistencies.
Face Morphing Detection Techniques
To detect a face morphing attempt, KYC Identity Verification Solution Providers employ the following methods:
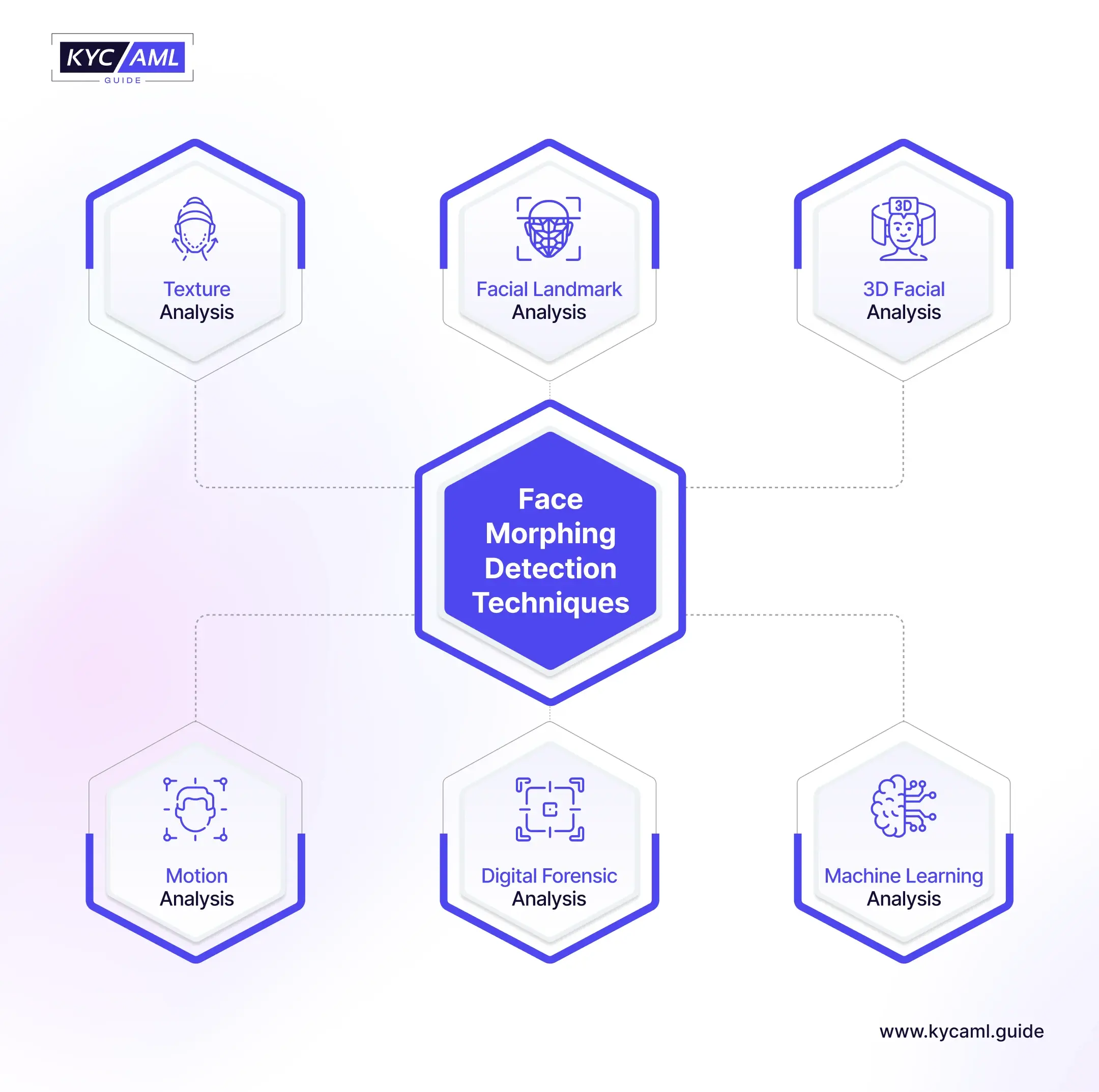
| Texture Analysis | KYC Identification Tools analyze the texture and pixel-level details of the identity images to detect inconsistencies and anomalies occurring during morphing. |
| Facial Landmark Analysis | A deep analysis of Facial Landmarks can also help in detecting morphed images. Facial Biometric identity verification tools can analyze different facial features and landmarks for the detection of morphing. |
| 3D Facial Analysis | Three-dimensional analysis of facial features with 3D modeling helps in detecting various morphing techniques. |
| Motion Analysis | Some cutting-edge KYC Identity Tools also detect facial movements and behavior including gestures that detect unnatural movements and morphed content. |
| Digital Forensic Method | Utilizing digital devices to detect the traces of manipulation in an image or a video. |
| Machine Learning Algorithms | Machine Learning models are trained on the given datasets or genuine and morphed images to differentiate between the two accurately. It enhances the ability of a biometric identification variable, especially in facial biometrics. |
How to Prevent Facial Morphing Attacks?
Differentiating between Real vs Fake Images over the internet is becoming increasingly difficult. This is due to the alarming number of facial morphing attacks, deepfake attacks, and other artificial identity attacks. Preventing Facial Morphing is one of the critical aspects of securing online identities and preventing other crimes. Here are a few ways in which Morphing attacks can be prevented and user identities can be secured.
|
|
|
|
Furthermore, there are benchmarks set by NIST for KYC Solutions to scale their Differential Morphing Detection parameters. After implementing these benchmarks KYC Identity Solution Providers can play a vital role in mitigating the threat of morph attacks. Since morphing is used to create deepfakes which are used for fraud and other illicit criminal activities, they pose a serious threat to the financial integrity and customer’s security. Therefore, preventing morphing is crucially important where KYC Tool providers through their vigilance can help in the detection and prevention of morph attacks.
Also Read: Everything you need to know about Face Identity Verification





