Age verification is to verify the age of the user by providing a date of birth or checking a box to indicate that you are age-appropriate to use the services or products offered by the company. It is required by many industries such as gaming sites, mobile banking, social networking, e-commerce, etc.
The following are the best practices for implementing KYC Age Verification.
1 Understanding Legal Compliance:
Many countries have laws and regulations regarding the access and distribution of products and services, often requiring age restrictions to ensure compliance. The bill was introduced for the protection of children from harmful content by the UK government as an Online Safety Bill. Protecting children from online misuse is one of the hot topics in the US; the effort to protect children from this is age verification. The efforts were made at the federal level and laws were made for children’s protection online and kept the children safe with the Children’s Online Privacy Protection Act (COPPA) and related regulations. Additionally, acts like the Tobacco 21 legislation were established to prohibit the selling of tobacco products to people under the age of 21, and the National Minimum Drinking Age Act of 1984 ( according to the CDC) set the minimum age for alcohol consumption to be 21.
2 Document Check:
An online ID card is one of the most reliable age verification methods. The built-in advanced OCR engine can scan a copy of the user ID and display the holder’s age if needed. The analysis is performed by the tool to determine the age of a person based on the documents providing the date of birth. As part of the KYC onboarding flow a scanned copy of the users’ ID card as well as a photo of their ID was sent. The solution retrieves data from the field of view such as passport number, date of birth, name, etc. but also helps in reading and validating the document with different features of security such as barcodes and Machine-readable zone (MRZ).
3 Biometric Verification
Biometric verification is the next level above the secure verification of identity documents, as it verifies that the document belongs to the owner. In practice, users are asked to look into the camera and take a selfie. The resulting image is used to compare the image in the documents. A rule of thumb is also to conduct a liveness check. Given the advances in visual technology that make it possible to create realistic and deep masks, such research is needed to ensure that there is a real person in front of the camera. In general, an identity document and biometric data together are the most reliable and complete way to identify a person, verify his identity, and ensure that he is a real person who is also of legal age.
4 Face Matching
Face matching is a very important step in the verification process. It determines whether the person matches the photo of the person in the document. Without this system, a 10-year-old can easily take advantage of your parents. Document checking is done by the person who is for example a bouncer at a nightclub, a bartender, or a store clerk, and he ensures that the ID matches the person standing or sitting in front of them. It is really obvious if the 10-year-old child tries to buy alcohol with his parents’ ID card. Face matching can be done using automated systems or trained experts called super-recognizers. Many people can combine their identity with their face on their recent identity document. However, many people find it difficult to connect today’s selfies with nine-year-old documents. Therefore, super-recognizers must be thoroughly inspected and continuously trained. Companies must continuously conduct quality assurance and internal audits.
5 Risk Assessment:
Imagine you are an online blogging community where certain content is only suitable for users of a certain age. An age-appropriate risk assessment is like a parenting helmet that is well-protected and shielded. It’s worth stepping back for a moment and considering the potential risks. Some young writers may find themselves in adult content or in legal trouble for not conforming to the age guidelines. Imagine if this study gave writers a place to write. How to register (make sure they’re honest about their age), protect their information as a best-kept secret, and make sure the platform doesn’t experience any technical glitches or misunderstandings that could send the wrong message to the wrong person. It’s about making your creative side good, fun, and relevant, just like a responsible guard uses for his job.
What is Age Verification Used for?
The KYC process usually includes age verification. KYC is a mandatory process for onboarding new customers in banks and other highly regulated sectors. In such cases, age verification is only one aspect of identity verification. Age verification is often required in sectors such as e-commerce where there are no KYC standards but age-sensitive products and services are sold. It is not necessary to verify the identity of customers, but businesses need to ensure that they are interacting with adults.
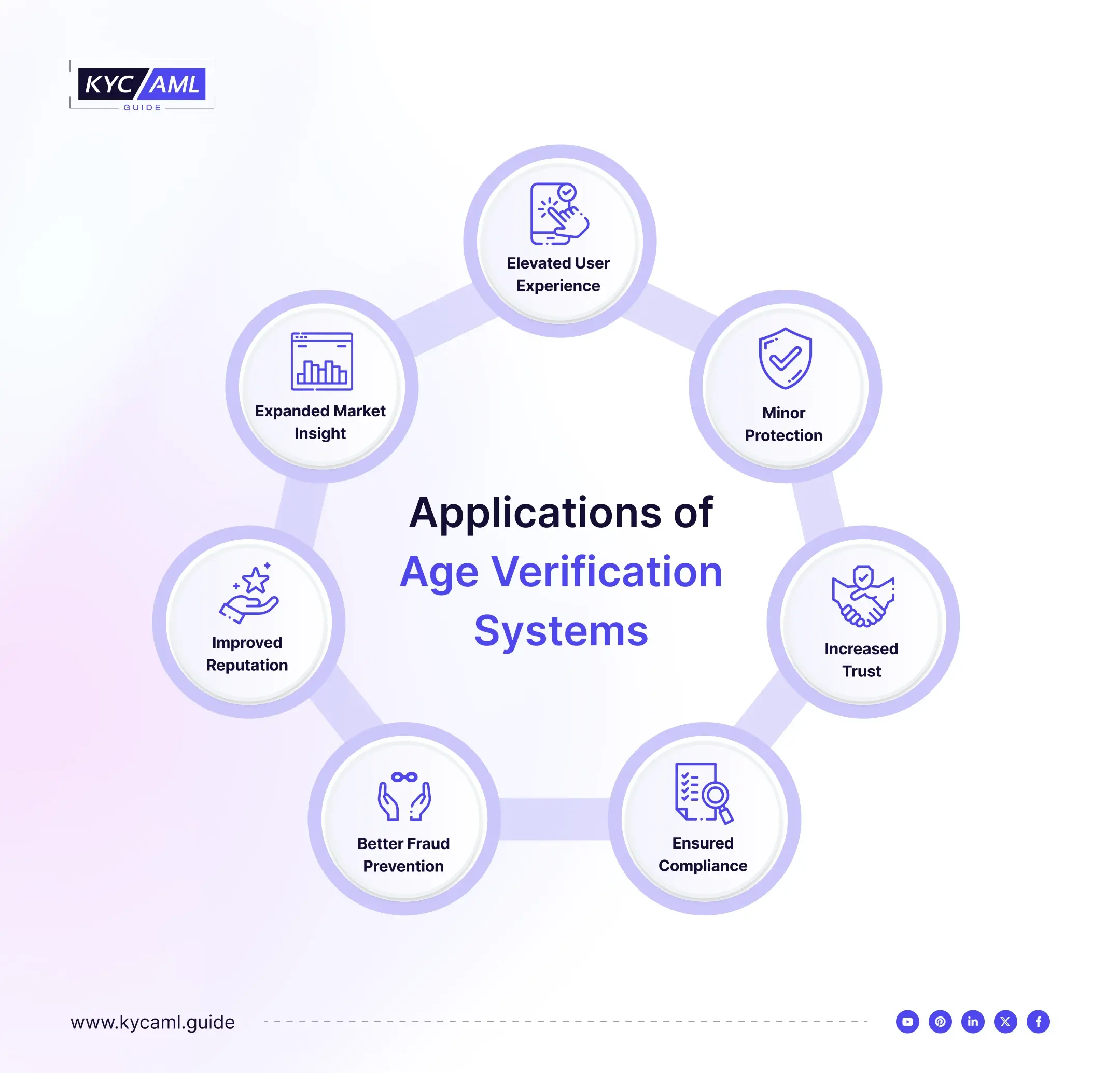
Additionally, age verification may be required for authorization as an additional security measure. For example, an online casino can verify that the person trying to log into the account is the same person who created the account. They can carry out identity checks for this purpose. Therefore, children cannot log in even if they have access to their parents’ device, password, or ID. Finally, sometimes you need to know a customer’s age, but asking for their ID for verification is too much to ask. For example, some supermarkets may collect customer information to gain insight into their target group. They don’t match the specific ages of customers, but they can use smart cameras to collect statistical data. Facial recognition technology makes this possible (although it may be illegal in some countries).
Choose a Trusted Age Verification Provider with our KYC AML Guide
Age verification is an advanced process that uses the most advanced digital technologies, such as artificial intelligence, biometrics, facial recognition, gesture recognition, etc. Extracting information from user-submitted documents requires accuracy, which increases the effectiveness of the document. not be fake or deceptive and compare the information with various relevant databases. KYC AML guide can help you choose the right KYC solution by offering research-based KYC technology buying and KYC vendor analysis.





