Vendor due diligence also known as vendor risk assessment is the act of assessing potential vendors to make sure that they are reliable and valuable for your business. Even though it might appear to be basic, there is something else to the due diligence process besides what initially meets the eye. You want to consider factors, for example, reputational, operational, and cyber risks before you feel sure working with a new vendor.
Great vendor relationships are significant resources for any organization, while poor vendor relationships can be exorbitant. Without doing homework, it is impossible to know which vendor will be the best accomplice for your business. Vendor due diligence is not a one-time task. You ought to consistently audit and update your vendor due diligence checklist to stay up-to-date with the changing requirements and emerging threats.
Vendor Due Diligence Checklist
A vendor due diligence checklist is the process an organization follows to perform due diligence on third parties. VDD is a comprehensive investigation or evaluation to investigate a vendor with whom you are planning to enter into a contract. Accept a vendor only if you are convinced that it can meet or improve your requirements and expectations. Once a vendor is onboard, continue to monitor their cybersecurity risk. However, regardless of how the risk assessment is done, there are many important factors to consider. Below is a detailed vendor due diligence checklist that can help you identify potential risks and vulnerabilities in several ways.
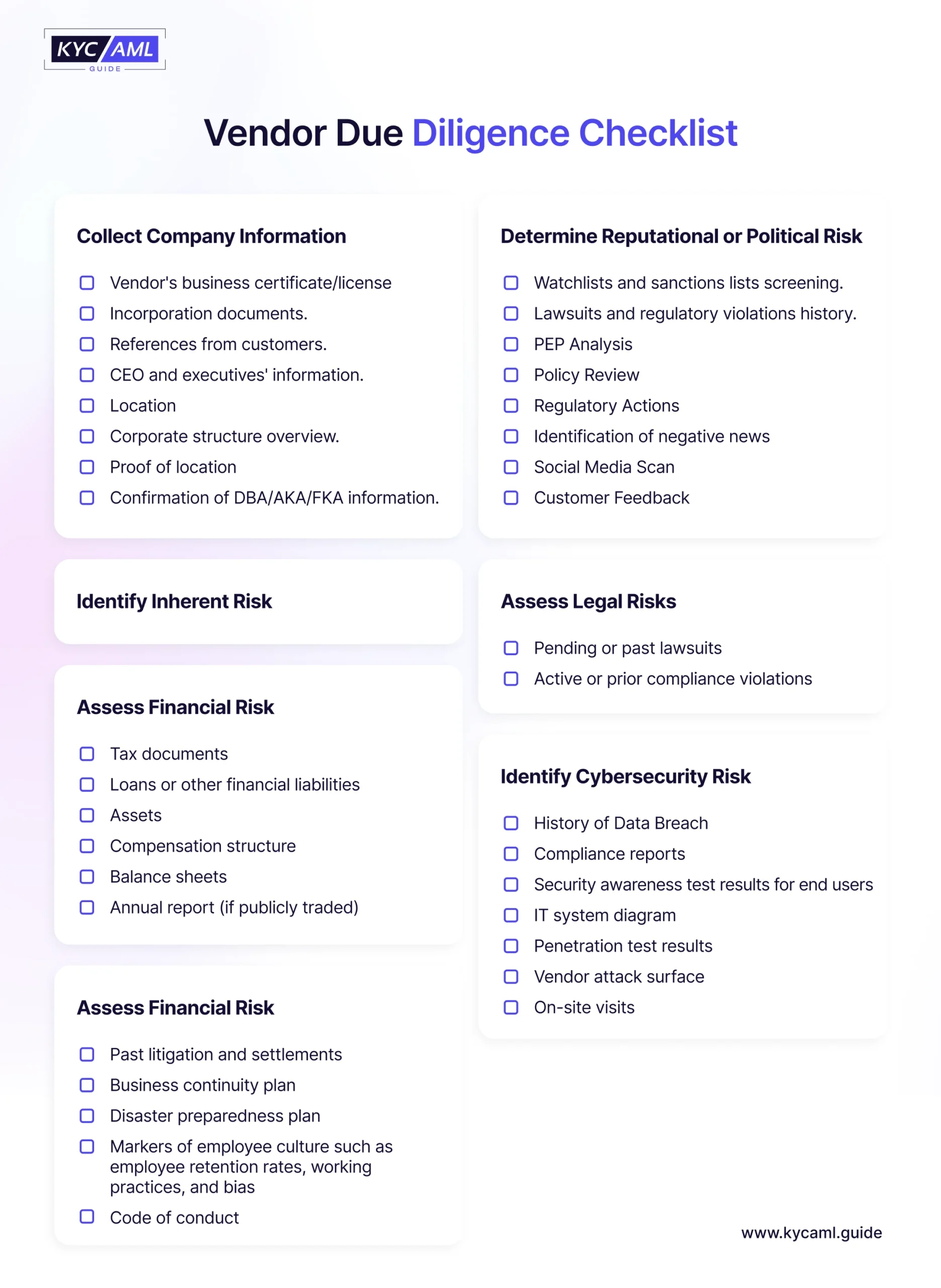
1) Collect Company Information
Before onboarding a vendor the initial step is to gather basic information about the organization. By collecting basic information about the vendor you can confirm that the organization is legitimate and authorized to carry on with work in your space. You should also collect information on key personnel for future risk assessments included
- Vendor’s business certificate or license- In the UK this information is available on Companies House and in the US through the Securities and Exchange Commission (SEC) and is known as EDGAR.
- Incorporation documents
- References from some of the vendor’s customers
- Basic information on the vendor’s CEO and other executives or board members
- Location- are they located in a high-risk country
- An overview of the vendor’s corporate structure
- Proof of location, such as photographs or an on-site visit
- Confirm any ‘doing business as’ (dba), ‘also known as’ (aka), or ‘formerly known as’ (fka) information to get a comprehensive picture of the vendor business identity.
While you may need to dig deeper when evaluating a vendor, this basic business information will form the basis of the rest of the vendor risk management process.
2) Identify Inherent Risk
Inherent risk is the risk that the vendor poses before your company takes mitigation measures. When trying to identify a vendor’s inherent risks, consider the following:
- How easy is it to change the vendor if something goes wrong?
- How much data and what type will you share with the vendor?
- How important is this vendor to your business?
- What’s the vendor’s reputation in the industry?
- In which geographical area does the vendor work and how does this impact the level of regulatory oversight and risk?
Other examples of inherent risks are Inadequate cybersecurity practices, operational inefficiencies, and poor financial conditions and it is important to recognize them early.
3) Assess Financial Risk
If the vendor you work with goes bankrupt or you suddenly have to lay off key team members, your company will be in crisis. This makes it important to carefully review the vendor’s financial information to assess vendor financial risks such as
- Tax documents
- Loans or other financial liabilities
- Assets
- Compensation structure
- Balance sheets
- Annual report (if publicly traded)
4) Assess Operational Risk
Operational risks are risks that naturally exist in the vendor’s operations. For example, a vendor in a hurricane-prone location is at risk of closing due to weather. A vendor that relies on a complex supply chain may be at risk of closure due to supply chain disruptions. To help identify a supplier’s operational risks, ask about the following things;
- Past litigation and settlements
- Business continuity plan
- Disaster preparedness plan
- Markers of employee culture such as employee retention rates, working practices, and bias
- Code of conduct
5) Determine Reputational or Political Risk
At the point when you decide to team up with a vendor, you’re entrusting a part of your business to their hand. Assume news spreads that your organization is working with a shady vendor it will harm your organization’s reputation. Also working with untrustworthy vendors can cause immediate chaos. Penalties and lawsuits can damage the vendor’s operation and ruin your business. By carefully checking these things, you can ensure that the vendors are properly checked, reducing the risk to the business. Check out the following:
- Watch lists and sanctions lists
- Lawsuits and regulatory violations
- Politically Exposed Persons (PEP) and law enforcement lists
- Review the vendor’s internal policies and procedures related to risk management and data security.
- Obtain and assess any relevant reports or actions taken against the vendor by regulatory agencies such as the Consumer Financial Protection Bureau (CFPB).
- Look for negative news or stories about the vendor’s company, especially if they involve security breaches or immoral behavior.
- Review the vendor’s social media activity and look for red flags or controversial statements or behaviors.
- Check customer complaints and negative reviews both online and offline about the vendor’s services or practices.
6) Assess Legal Risks
Legal risks are connected with reputational and political risks. Although your organization isn’t answerable for criminal operations of vendors, for example, money laundering or fraud, these activities can in any case have bad results for your organization. See
- Pending or past lawsuits
- Active or prior compliance violations
7) Identify Cybersecurity Risk
Data breach protection is critical for all businesses with over 450,000 new cases of malware per day. Indeed, with strong cybersecurity measures set up, data exposure risk can happen when you work with a vendor with lax cybersecurity measures. A risk-based plan is required, which requires an evaluation of the vendor’s compliance with cybersecurity standards, for example, ISO 27001. Besides, third-party cyber breaches are progressively common and exorbitant, featuring the need to consider third-party cyber risk in the procurement process. Key variables to consider while conducting a third-party cybersecurity risk assessment are:
- History of Data Breach
- Compliance reports– has the vendor adopted a cyber security framework such as NIST or SOC2? Do they comply with regulations such as GDPR, DORA, or NIS 2?
- Security awareness test results for end users
- IT system diagram
- Penetration test results
- Vendor attack surface
- On-site visits to verify security may be required for high-tier vendors such as those providing critical services or accessing sensitive data.
What’s Next?
A vendor due diligence checklist is vital to distinguish likely dangers and to guarantee that the vendor can depend on the standards and expectations of the contracting organization, hence safeguarding the organization’s interest. When the information has been gathered adequately for the Vendor Due Diligence process, the subsequent stage is to conduct a thorough verification of this information. This includes organizing data according to recognized best practices and carefully analyzing it in the context of your organization’s risk tolerance. This detailed analysis will help you make a clear decision about continuing the vendor relationship.
Strategies for Regular Review and Updating of Vendor Due Diligence Checklist
A Identifying Vendor Risks:
When evaluating vendors, consider potential risks such as operational, financial, legal, reputational, cybersecurity, and environmental impacts. For those responsible for sensitive data, focus more on critical areas such as cybersecurity and address these risks based on vendor performance. You can categorize them as follows:
| General Vendors | vendors who don’t have access to your network or your data |
| Confidential/sensitive data Vendors | Vendors have access to sensitive or confidential information |
| Strategic Vendors | Vendors without whom you can’t do business |
B Assessing Vendor Risk Levels:
Evaluate vendors based on size, location, service, certification, history, and performance. Use a ranking system to identify high-risk vendors and ensure vendor due diligence.
C Reviewing Due Diligence Checklist:
Update the vendor due diligence checklist regularly to meet business requirements and standards for all relevant aspects of vendor evaluation.
D Conducting Vendor Due Diligence:
Collect vendor data through interviews, surveys, and reviews. Monitor your results and consider using more powerful software for efficiency.
E Analyzing and Reporting Results:
Monitor data for warning signs and report findings to stakeholders. Use visual aids, such as charts or reports for clarity.
F Monitoring and Updating Due Diligence:
Continually monitor vendor performance and develop due diligence processes to adapt to changing conditions
Need Help Managing Relationships with Vendors?
If you’re hoping to improve how you deal with your vendor contracts, the KYC AML guide could help you benefit from their vendor analysis consultancy. Our experts are enthusiastic about assisting your company in achieving the assurance it deserves.





