What is KYC Outsourcing?
KYC outsourcing is the practice of contracting out Know Your Customer (KYC) and anti-money laundering (AML) procedures to third-party service providers. This includes services like document identification and verification, blacklisting, and risk assessment. Companies can gain access to professional services, increase safety, save money, and work more efficiently by outsourcing these services. However, there are potential pitfalls, such as data loss and reliance on third-party vendors, which necessitate careful vendor selection and management to ensure data protection and processing. 48% of organizations report difficulty tracking third-party compliance and a complete list of all third parties with network access.
The Changing Landscape of Customer Security
Businesses face several challenges as customer security expectations continue to evolve. Nonetheless, it is precisely these challenges that are driving the transformation of compliance and fraud prevention. There are growing concerns about data confidentiality and privacy. As a result, businesses are emphasizing KYC customer service outsourcing. Companies have made significant investments in advanced technology and highly skilled professionals as a result of the increase in fraud activity. These investments are aimed at detecting and preventing fraudulent activities, as well as ensuring the business’s integrity.
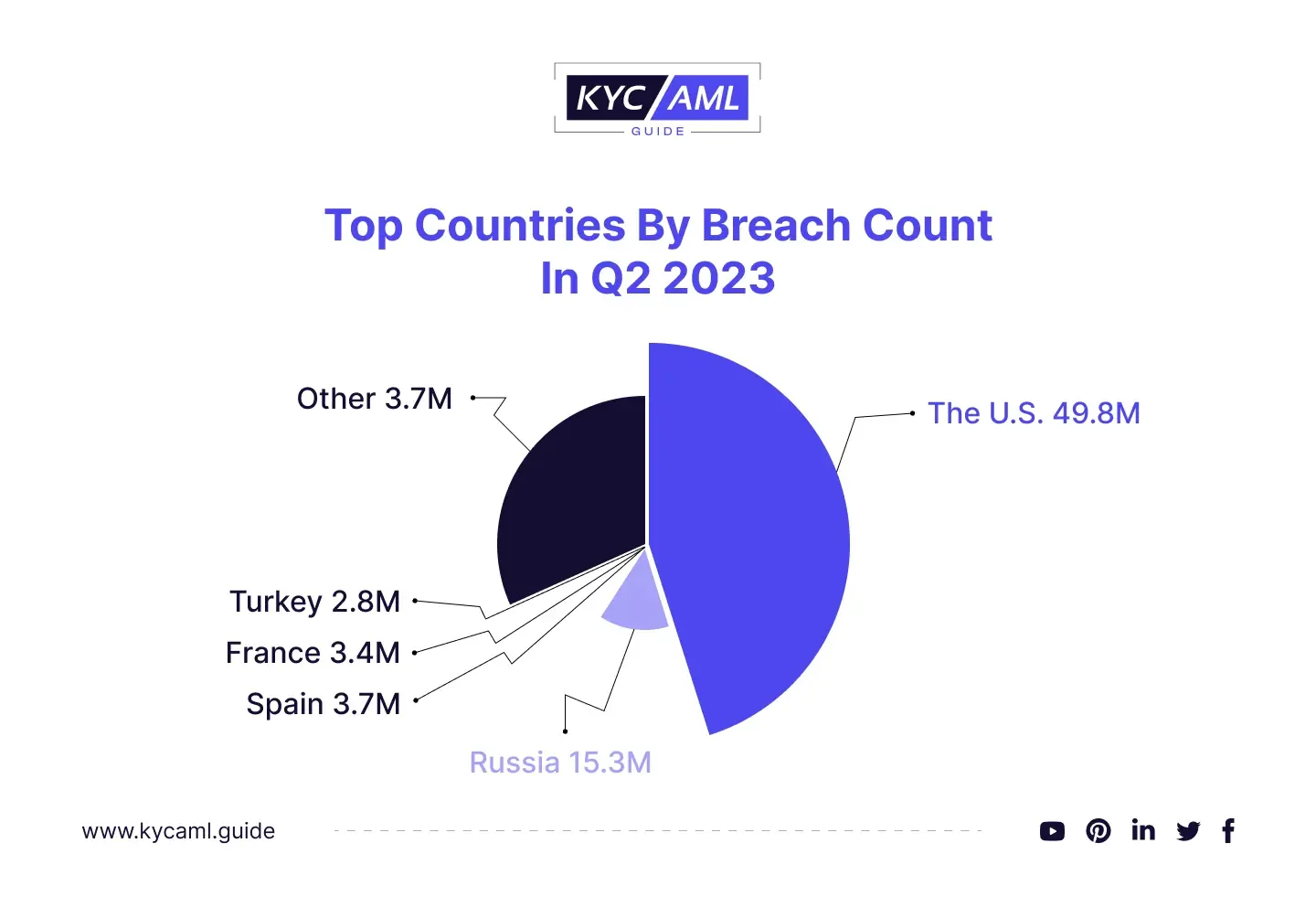
A significant increase in data breaches was seen in the second quarter of 2023 when there were 2.6 times as many as in the quarter before. This quarter saw a 156% increase in breached accounts, totaling a staggering 110.8 million compromised accounts. To put this in context, this equates to an alarming rate of 855 accounts being leaked every minute. According to the Office for Civil Rights of the US government, healthcare organizations reported 145 data breaches in the first quarter of 2023,
An unsettling trend emerged this quarter across multiple countries. Notably, leaked accounts were most common in the United States, Russia, Spain, France, and Turkey. Except for Turkey, these same countries were also among the top five most breached nations in the previous quarter.
External-facing assets such as servers and databases, in particular, contribute significantly to this risk, accounting for 12% of data breaches. The lack of security measures for these external-facing assets is one of the top three root causes of data breaches, posing a significant and serious threat to businesses.
Also Read: The Role of Cybersecurity in KYC and AML Compliance
The Importance of Data Security and Privacy in KYC Outsourcing
KYC customer service outsourcing has many advantages but it also has risks related to data security and privacy. 90% of compliance professionals in the Philippines, Mexico, Thailand, Indonesia, China, and Vietnam believe that privacy regulations benefit their businesses. When selecting and collaborating with KYC service providers, financial institutions should carefully consider these factors.
Regulatory Compliance
Complying with data protection laws and non-negotiable financial regulations. Check that your partner follows the same standards and can demonstrate compliance through certification and audits. 58% of compliance teams say the most difficult aspect of third-party risk management is determining vendor responsiveness.
Data Encryption
To prevent unauthorized access to confidential customer information, all transmissions and data storage must be encrypted. This includes both data in transit and data at rest.
Access Control
Implement strict access controls to limit who can see and change customer data. Only the information must be accessible to third-party employees. Third parties gaining unauthorized access to a company’s network account for 15% of all security breaches.
Data Residency
Consider the database’s location. Check that it meets regulatory requirements and provides the level of data protection that your customers expect. According to 52% of compliance experts, a lack of data and information about partners exposes a company to third-party risks.
Incident Response
Create detailed procedures for dealing with data breaches and security incidents. Your partner should have a solid incident response plan in place to limit damage and protect those who are affected.
Vendor Risk Assessment
Conduct a thorough investigation into the third party’s security measures and practices. Examine your cybersecurity policy, employee training, and previous experience protecting customer data.
Regular Audits
Ongoing monitoring and auditing of the security practices of the KYC outsourcing partner aid in data security. Regular audits ensure that the partner is still meeting security and compliance requirements.
Data Retention and Disposal
Establish clear policies for retaining and disposing of customer data. Data should not be kept for any longer than is necessary, and secure disposal methods should be used.
Also Read: KYC Outsourcing vs. In-house Systems Pros and Cons
Building Trust through Transparency
The Data Protection Act of 2018, which replaced the 1998 version and is aligned with the GDPR of the EU, governs the responsible collection, use, control, and processing of individuals’ data, guiding entities such as businesses and governments. This act, guided by seven principles, ensures that data is used lawfully and transparently. It also builds trust with stakeholders and customers, increasing user confidence and emphasizing the importance of robust KYC and AML systems in preventing illicit financial activities.
Transparency is essential for fostering trust among financial institutions, their customers, and KYC customer service providers. To ensure comprehension, follow these steps:
- Customers should be informed about data management practices, such as how their information will be used and stored.
- Maintain open lines of communication with your third-party partner while performing regular audits and inspections to ensure compliance.
- Keep up to date on changes in data protection laws and adapt your practices accordingly.
Conclusion
KYC outsourcing can be a useful tool for financial institutions looking to improve operational efficiency and regulatory compliance. However, during outsourcing relationships, data security and privacy must be prioritized. Financial institutions can navigate the complexities of outsourcing KYC while protecting their sensitive customer data by selecting reputable partners, implementing strong security measures, and maintaining transparency.





